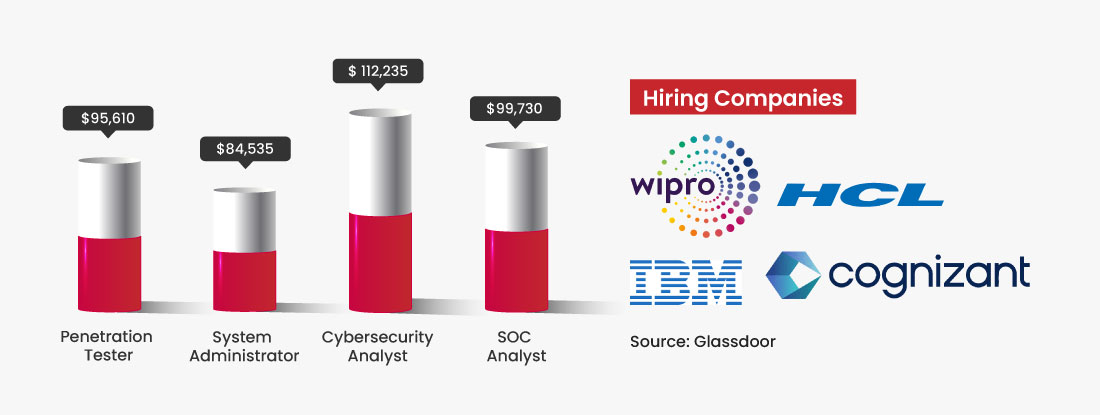
Cyber Security Expert Online Training
The Cybersecurity Expert Training Program is the only program that covers both offensive and defensive security in a practical hands-on setup. The course will cover SOC concepts as well as fundamentals of ethical hacking and penetration testing. Top tools covered in this course are – Splunk, 69phisher, NMap, Metasploit and many more.















 5th Sep: Weekend
5th Sep: Weekend 



 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.






 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
