Certified Information Privacy Technologist (CIPT) Certification Training
 Read Reviews
Read Reviews
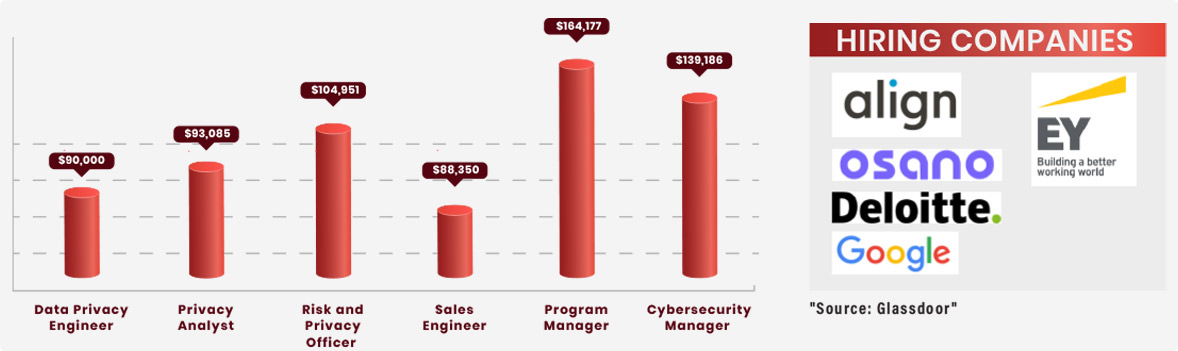
Certified Information Privacy Technologist (CIPT) certification is developed by the International Association of Privacy Professionals (IAPP) to certify the knowledge of privacy-related concerns and procedures in relation to the development and use of information and communication technology. For IT professionals who want to learn more about privacy needs in technology, obtaining the CIPT certificate is a smart first step. The CIPT certification training from InfosecTrain will provide you the proper understanding of privacy related issues.





 5th Sep: Weekend
5th Sep: Weekend 





 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.






 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
