OT/ICS Security Foundation Training
 Read Reviews
Read Reviews
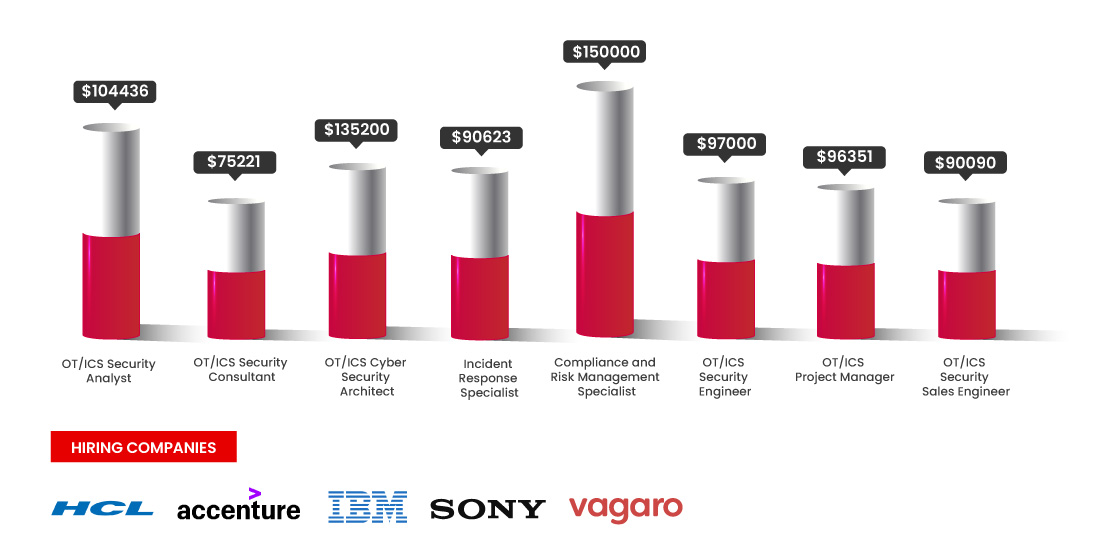
Hardware and software systems that communicate with the physical world are collectively referred to as operational technology (OT). With a desire to integrate IT skills into physical systems that either replace or enhance the current physical control components, it has developed steadily through time. The evolution of OT has been facilitated by technologies like smart buildings, smart transportation, and the Internet of Things, which have reduced costs and improved performance. This development indicates a rising need for professionals with the knowledge and skills to deal with OT.





 5th Sep: Weekend
5th Sep: Weekend 




 The sessions are so great and instructor explanation was excellent.
The sessions are so great and instructor explanation was excellent.



 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
