The courseware of CEH v11 Certification Training is designed to provide you a strong and deep understanding of various verticals of security, starting with preparing a base and advancing to the latest scenarios. Provided is the list of modules with a brief description of what it talks about.
Module 01: Introduction to Ethical Hacking: This module introduces you to the basic concepts of hacking, what is hacking, who are hackers, their intent, and other related terminologies.
The next modules dive deeper into the various phases of hacking, which would help you in thinking with the mindset of a hacker.
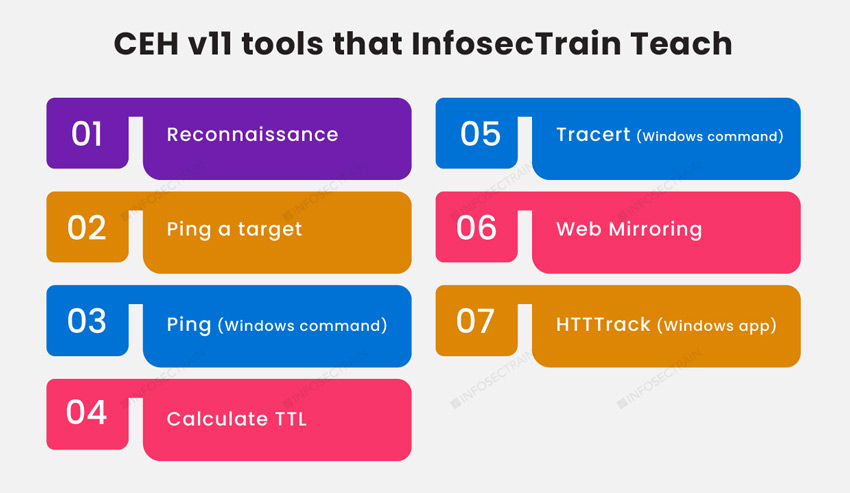
Module 02: Footprinting and Reconnaissance: Gathering information from various sources using footprinting tools and how to defend against the same.
Module 03: Scanning Networks: Different techniques to identify and scan the network, host, and port discovery by utilizing various scanning tools.
Module 04: Enumeration: Finding detailed information about the hosts and ports discovered during scanning. This module now includes sub-domains like NFS enumeration and related tools, DNS cache snooping, and DNSSEC Zone walking, along with the countermeasures.
Module 05: Vulnerability Analysis: It introduces the concepts of vulnerability assessment, its types, along with a hands-on experience of tools that are currently used in the industry.
Module 06: System Hacking: It focuses on the “how” part. How to gain access of the system, how to escalate privileges, how to maintain access, and how to clear your tracks.
The next modules help to develop a deeper understanding of various defense and attack methodologies and concepts that aid the process of hacking.
Module 07: Malware Threats: Malware threat terminologies, viruses, worms, trojans, their analysis, and countermeasures to prevent data loss. The introduction and analysis of malware like, Emotet and fileless that are gaining popularity have been updated under this section. APT concepts have also been added.
Module 08: Sniffing: Packet sniffing techniques, associated tools, and related defensive techniques.
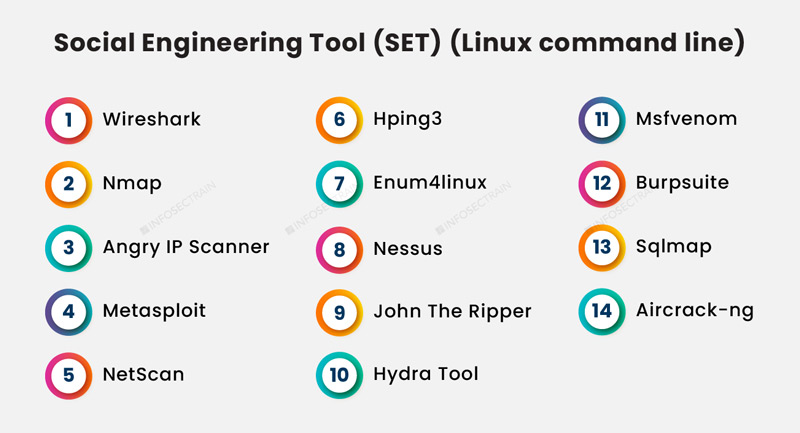
Module 09: Social Engineering: Since humans are the most significant vulnerability for any organization, it becomes essential to understand how attackers use them for their purpose for carrying out attacks like identity theft, impersonation, insider threat, and how to defend against such social engineering attacks.
Module 10: Denial-of-Service: As DoS and DDoS are some of the most common purposes of attackers, this module talks about these attacks, use cases, and the related attack and defense tools.
Module 11: Session Hijacking: To provide a deeper understanding of the technique, its purpose, tools used along with the countermeasures.
Module 12: Evading IDS, Firewalls, and Honeypots: Understand the terminologies and working of these inline defenses and techniques to learn how to evade these while performing an attack.
Module 13: Hacking Web Servers: Web servers based attacks, methodologies, tools used, and defense
Module 14: Hacking Web Applications: Web application-based attacks, techniques, and mitigation.
Module 15: SQL Injection: An in-depth understanding of the top OWASP top 10 web app vulnerability, it’s working and the mitigation.
Module 16: Hacking Wireless Networks: Wireless encryption, wireless hacking, and Bluetooth hacking-related concepts
Module 17: Hacking Mobile Platforms: Management of mobile devices, mobile platform attack vectors, and vulnerabilities related to Android and iOS systems
Module 18: IoT Hacking: Recognizing the vulnerabilities in IoT and ensuring the safety of IoT devices. Operational Technology (OT) essentials, introduction to ICS, SCADA, and PLC, threats, attack methodologies, and attack prevention. The concept of OT is a new addition.
Module 19: Cloud Computing: Cloud computing, threats, and security. Additionally, the essentials of container technology and serverless computing have been added.
Module 20: Cryptography: Encryption algorithms, Public Key Infrastructure (PKI), cryptographic attacks, and cryptanalysis.
 Read Reviews
Read Reviews





 5th Sep: Weekend
5th Sep: Weekend 






 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.






 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
