Cybersecurity Data Science Training Course
 Read Reviews
Read Reviews
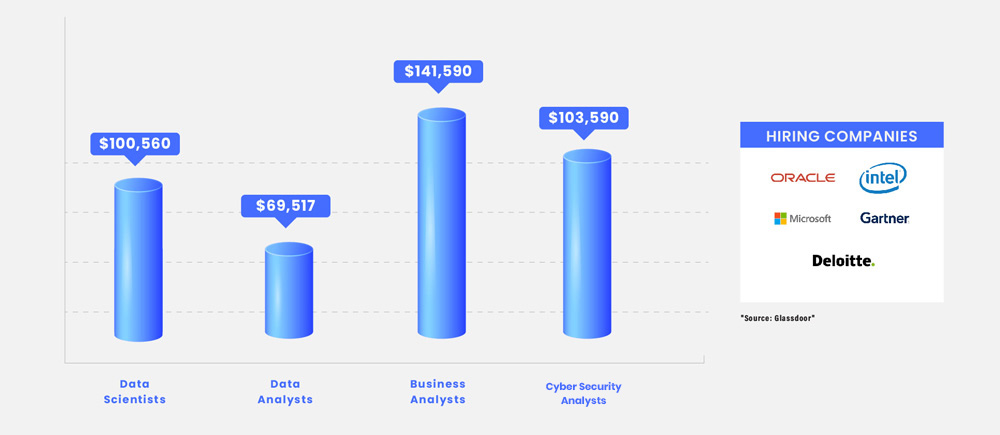
Data Science is regarded as one of the most in-demand careers today. It is also one of the most fascinating and diversified IT careers in the world, with premium packages that attract attention. The majority of cyber-attacks compromise a company’s stored data and use it for fraudulent purposes. Data security is at the heart of cybersecurity. Cybersecurity Data Science training course from Infosectrain is a novel approach to using data science to detect, prevent, and mitigate cybersecurity threats.





 5th Sep: Weekend
5th Sep: Weekend 




 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.






 Certified & Experienced Instructors
Certified & Experienced Instructors Post Training Support
Post Training Support Customized Training
Customized Training Flexible Schedule
Flexible Schedule Access to Recorded Sessions
Access to Recorded Sessions 



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
