How to Become an Information Security Analyst

What is an Information Security Analyst?
Today we need more specialists to protect our data as we keep and share more data online. Cybercriminals and attackers regularly threaten our digital world by stealing sensitive information, compromising online security systems, and putting people’s online presence at risk. Hence, Information Security Analysts are in high demand to safeguard one of the most significant resources and data in an organization.
In the 21st century, major data breaches at large corporations have already occurred, exposing the personal information such as credit card information, credentials, and security numbers of hundreds of millions of people. Information Security Analysts protect businesses from threats like data theft and cybercrime.
Roles and Responsibilities of an Information Security Analyst
The Information Security Analyst’s primary role is to develop sustainable security systems to handle and prevent risks. However, the roles and responsibilities of an Information Security Analyst vary by the business, which is frequently on call in the event of data breaches, hacking, or other emergencies involving the security of digital assets. The following are the roles and responsibilities of an Information Security Analyst in general:
- They identify, monitor, and resolve security issues such as physical security, software security, and network security.
- They establish and maintain organizational firewalls.
- They control credentials and file access.
- They are aware of new risks in the cybersecurity domain through engagement with outside parties.
- They engage with other teams and management to implement the best security practices within an organization.
- They conduct network system audits.
- They are competent at ethical hacking.
Skills of an Information Security Analyst
An Information Security Analyst must possess several crucial skills. So, in this part, we will go through some of the most popular skills for an Information Security Analyst:
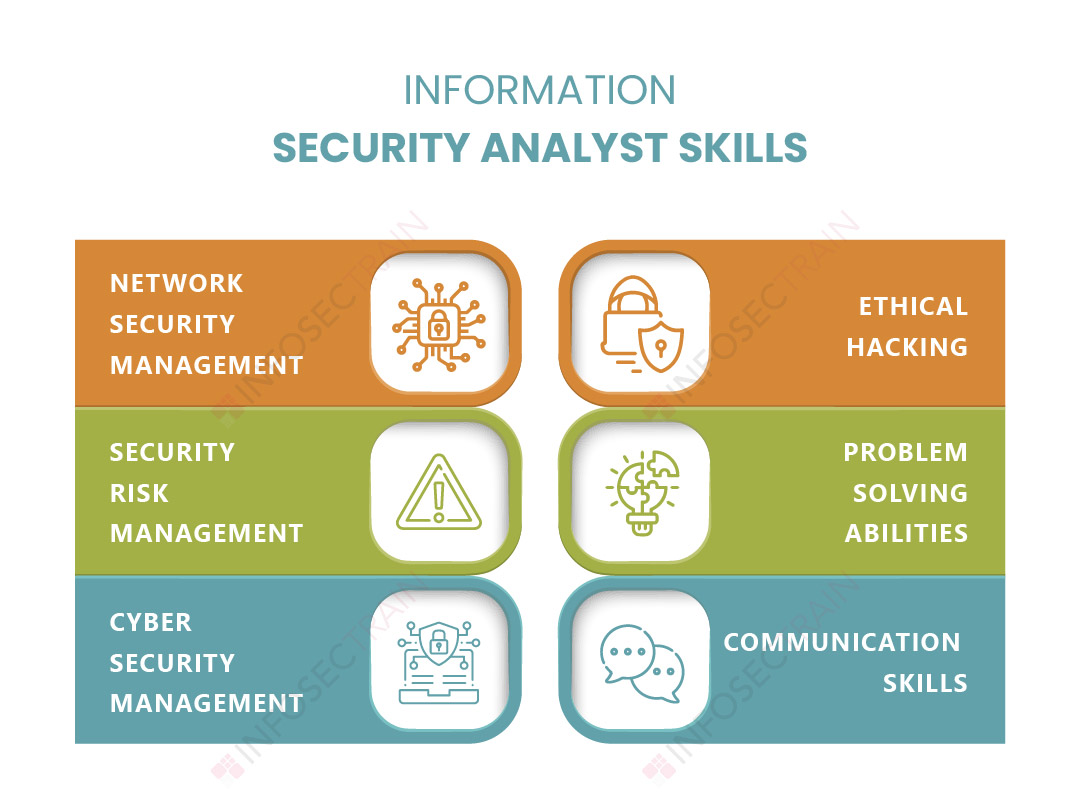
- Network security management: Information Security Analysts keep the company’s network secure through testing and eliminating potential threats regularly. In most situations, they supervise a team of IT experts and report to upper management, serving as a technical translator.
- Security risk management: Information Security Analysts evaluate security risks, possible external threats, and weaknesses in the company’s network. They also develop ways to deal with threats of all types and sizes.
- Cyber security expertise: An Information Security Analyst is the cyber security expert in any organization. The position necessitates a foundation in cybersecurity essentials, such as ethical hacking, coding, etc.
- Ethical hacking: To defeat attackers, an Information Security Analyst must think critically like attackers. You must understand ethical hacking to find vulnerabilities in the system or network.
- Problem-solving abilities: As an Information Security Analyst, you must have the ability to solve problems in order to provide realistic and long-term solutions.
- Communication skills: Effective communication is crucial in every profession, but an Information Security Analyst has a special communication requirement. The Information Security Analyst must communicate technical network concepts and share issues to top management and executives in a clear and understandable manner.
Job Prospects of Information Security Analyst
Since information security is a priority for businesses worldwide, an Information Security Analyst who is well-trained and accredited is in great demand. As a result, career opportunities are numerous. The Bureau of Labor Statistics (BLS) report says that the employment of Information Security Analysts is expected to expand by 31% between 2019 and 2029, much faster than the national average. According to Indeed, the average salary for an Information Security Analyst is $81,065 per year, although this might vary depending on your experience and knowledge.
How to Become an Information Security Analyst?
Becoming an Information Security Analyst can open a new world of opportunities in the IT sector. However, most potential Information Security Analysts must first complete the following steps:
1. Obtain a bachelor’s degree: Most positions for Information Security Analysts require a bachelor’s degree in computer science or a related field. They must have a high level of expertise in information technology and security, and some companies prefer candidates with a master’s degree in a relevant subject. Obtaining a degree in cybersecurity or cloud computing might help prospective Information Security Analysts stand out in the job market and boost their chances of finding the job of their dreams.
2. Gain required experience: Most firms and organizations will require prior experience from Information Security Analysts. Individuals are advised to apply for positions in IT departments after completing their studies. Working as a Network or Systems Administrator is a common avenue for those interested in a career in security.
3. Acquire needed certification: Certification in information security is made up of a group of different certifications that, when combined, create foundational knowledge in a number of domains. InfosecTrain provides aspirants with the skills required to secure a network. Our security courses and certifications teach security professionals to identify vulnerabilities, defend against attacks, and respond quickly to incidents. Certifications for Information Security Analysts include:
- CompTIA Security+: The most fundamental credential for a career as an Information Security Analyst is the CompTIA Security+ It is a fundamental, vendor-neutral certification that certifies basic network security and risk management expertise.
|
|
TRAINING CALENDAR of Upcoming Batches For CISSP
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 12-Feb-2024 | 23-Feb-2024 | 07:00 - 12:00 IST | Weekday | Online | [ Open ] | |
| 15-Feb-2024 | 20-Mar-2024 | 08:00 - 10:00 IST | Weekday | Online | [ Open ] | |
| 24-Feb-2024 | 31-Mar-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 02-Mar-2024 | 07-Apr-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 11-Mar-2024 | 22-Mar-2024 | 07:00 - 12:00 IST | Weekday | Online | [ Open ] | |
| 16-Mar-2024 | 21-Apr-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Apr-2024 | 12-May-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 13-Apr-2024 | 19-May-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 01-Jun-2024 | 07-Jul-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |
|
TRAINING CALENDAR of Upcoming Batches For CISA
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 24-Feb-2024 | 24-Mar-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 16-Mar-2024 | 14-Apr-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 13-Apr-2024 | 12-May-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |
4. Choose the best path for you: After finishing your education and preparing to enter the world of cybersecurity, take some time to think about your chosen career path. Information security is crucial in various areas, including business, government, healthcare, telecommunications, and education. If you are interested in or have expertise in one of these industries, your new information security abilities may make you more marketable for employment in that industry.
Get Certified Today with InfosecTrain
The Information Security Analyst employment market is fully open, and the demand for IT and cybersecurity will continue to rise. Technical security experts with the appropriate training and qualifications can work in one of the world’s most diverse job marketplaces. The courses and training provided by InfosecTrain will assist in ensuring job security in a dynamic and complex information security industry. Enroll in our courses and get certified!







 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
