Maintaining an Information Security Management System (ISMS): ISO 27001 standard
ISO stands for International Organisation for Standardisation, founded in 1947, that builds standards for businesses and organizations in 163 countries worldwide. On an international level, ISO frequently collaborates with IEC (International Electrotechnical Commission). ISO makes documents with needed standards, specifications, and guidelines. These can consistently be used by companies and assures that materials, products, processes, and services are suitable for their target. Additionally, ISO ensures that these provisions are accepted in all connected countries to ensure standardization. With an ISO certification, companies prove that their products, services, or systems meet the recognized specifications. The ISO standards support innovation and improve worldwide quality, safety, and reliability.

What is the ISO 27001 standard?
ISO 27001 describes the requirements that an organization must apply to produce a model for establishing, executing, operating, monitoring, evaluating, and maintaining an Information Security Management System (ISMS). An ISMS is a framework of strategies and procedures that includes all legal, physical, and technical controls included in an organization’s information risk management processes. The ISO 27001 gives a checklist of controls that should be considered in the accompanying code of practice. This standard represents a comprehensive set of information security control objectives and a set of generally accepted good practice security controls. ISO 27001 is categorized into 12 separate sections:
- Introduction: It describes what information security is and why an association should manage risks.
- Scope: It covers high-level conditions for an ISMS to apply for all types of organizations.
- Normative References: This explains the correlation between ISO 27000 and 27001 standards.
- Terms and Definitions: It covers the complex technology that is used within the standard.
- Context of the Organization: It explains what stakeholders should be included in creating and maintaining the ISMS.
- Leadership: It defines how leaders within the organization should perform to ISMS policies and procedures.
- Planning: It covers how risk management should be planned crossed the organization.
- Support: It describes how to establish awareness about information security responsibilities.
- Operation: It includes how risks should be managed and how documentation should be implemented to meet audit standards.
- Performance Evaluation: It gives guidelines on how to control and measure the performance of the ISMS.
- Improvement: It explains how the ISMS should be continually updated and improved.
- Reference Control Objectives and Controls It provides an annex analyzing the individual elements of an audit.
ISO 27000 family
The ISO 27000 family has been progressively published since 2005. ISO 27001:2013 is the only certifiable standard of the ISO 27000 family. The other standards are guidelines.
- ISO 27000: This information security standard develops the basic concepts and the vocabulary that applies when analyzing Information Security Management Systems.
- ISO 27001: This information security standard defines the requirements of the Information Security Management Systems (ISMS).
- ISO 27002 (previously ISO 17799): Guide of best practices for information security management. This standard defines objectives and recommendations in terms of information security and anticipates meeting global concerns of organizations relating to information security for their overall activities.
- ISO 27003: Guide for implementing or setting up an ISMS.
- ISO 27004: Guide of metrics to facilitate ISMS management. It provides a method to define the objectives for implementation and effectiveness criteria of follow-up and evolution measurements all through the process.
- ISO 27005: Guide for information security risk management which complies with the concepts, models, and general processes specified in ISO 27001.
- ISO 27006: Guide for organizations auditing and certifying ISMS.
- ISO 27007: Guidelines for information security management systems auditing.
- ISO 27008: Guidelines for auditors on information security controls.
- ISO 27011: Guidelines for the use of ISO 27002 in the telecommunication industry.
- ISO 27031: Guidelines for information and communication technology readiness for business continuity.
- ISO 27799: Guidelines for the use of ISO 27002 in health informatics.
History of ISO 27001 series:
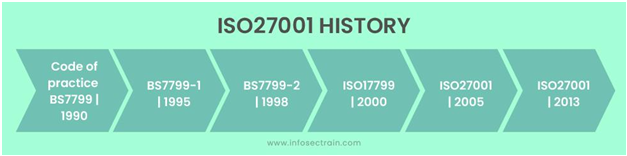
Note: The latest published version is – BS EN ISO/IEC 27001: 2017. The 2013 and 2017 ISO 27001 standards except for a few minor cosmetic points and a small name change.
What are the ISO 27001 Audit Controls?
The ISO 27001 standard lists security controls in three categories: preventive, detective, and corrective.
1) Preventive control
Goal: discourage or prevent the occurrence of problems
- Detect problems before they occur
- Control operations
- Prevent an error and malicious acts
2) Detective control
Goal: Search for and identify problems
- Use controls that detect and report the existence of an error and malicious act
3) Corrective control
Goal: Overcome the problems discovered and prevent the recurrence of problems
- Minimize the impact of a threat
- Overcome problems discovered by detection controls
- Identify the causes of the problem
- Correct errors arising from a problem
- Modify the processing system to reduce the presence of future problems to a minimum
How to Become ISO 27001 Certified?
To become ISO 27001 certified, you must attend a course and pass its final exam. The ISO 27001 certification exam covers both theoretical and situational questions, where the candidate must demonstrate how to apply the concepts learned. InfosecTrain provides certification training and necessary preparation guidance for ISO 27001 certification exams. It is one of the best consulting organizations, focusing on a wide range of IT security training. Highly skilled and qualified instructors with years of industry experience to deliver interactive training sessions on ISO 27001 standard certification exam. You can visit the following link to prepare for the certification exam.



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
