Empowering Threat Detection Capabilities with CTIA
Nowadays, the most severe attacks and data breaches result from very well-planned and complex attackers who target specific organizations and people. These attackers make the threat detection process very difficult because:
- Multi-phase campings and social engineering techniques cannot be easily detected by blocking or using simple threat indicators
- They continuously adapt new tactics, procedures, and tools to evade robust cybersecurity measures
They have also raised the bar high by systematically targeting the prey’s relevant business assets and data.

There are many strategies implemented to detect these threats. The strategies are:
- Collecting as many signatures, security events, and threat indicators as possible
- Using the same data to create alerts and monitor those alerts within the SOC using event management solutions and security information
- Hiring a SOC analyst who can examine the alerts
- Using the attack analysis to stop the progression of existing attacks
A few of these strategies failed, and others are less accurate.
The EC council has designed a certification course called CTIA(Certified Threat Intelligence Analyst) with the collaboration of threat intelligence and cybersecurity experts from across the globe. CTIA is introduced to help a business detect and alleviate its risks by converting the unknown external or internal threats into known threats. CTIA is an expert-level training that teaches a structured strategy for building efficient threat intelligence.
CTIA is a vital certification program for those who deal with threats daily. Nowadays, organizations are hiring professional Cybersecurity Threat Intelligence Analysts who can efficiently convert data into intelligence by implementing advanced strategies. Hence the scope of CTIA is accelerating day by day.
Incident Handling and Response Path:
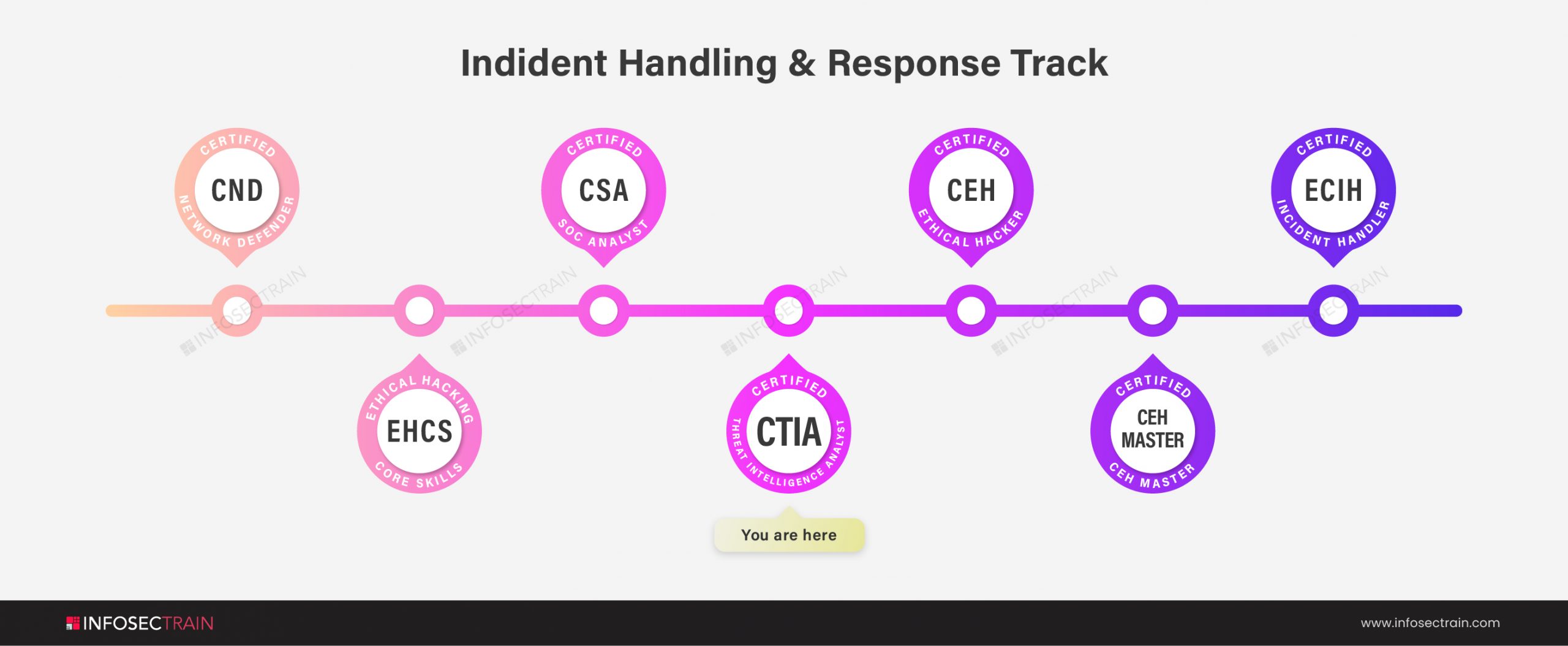
Note: This is a suggested career path to make your journey easy. But it is not mandatory to follow this path. You can take up the courses in any order.
Who can take this course?
- Incident response team
- Ethical hackers
- Mid to high-level Cybersecurity analyst with at least two years of experience
- Engineers, Analysts, Security practitioners, and Managers
- People from the Information Security profession who are willing to sharpen their skills in cyber threat intelligence
- Threat hunters
- Threat intelligence analysts, consultants, and researchers
- Malware analysts and digital forensics
- SOC professionals
In any organization, there are four types of teams, namely:
1. Red Team: Red teams are offensive players who hack into the organization to check the loopholes in the organization.
2. Blue Team: Blue teams are defensive players who protect the organization against the activities of the red team.
3. White Team: White teams play a referee role where they observe the activities of blue teams and red teams.
4. Purple Team: Purple team is a combination of Red teams and Blue teams.
Now, CTIA comes into the picture where Blue teams are working. CTIA helps blue teams by allowing them to understand the attackers efficiently and respond immediately. For SMBs, this information will help to protect the organization from the threats and risks successfully.
Now, three methods help us to detect the threat with CTIA they are:
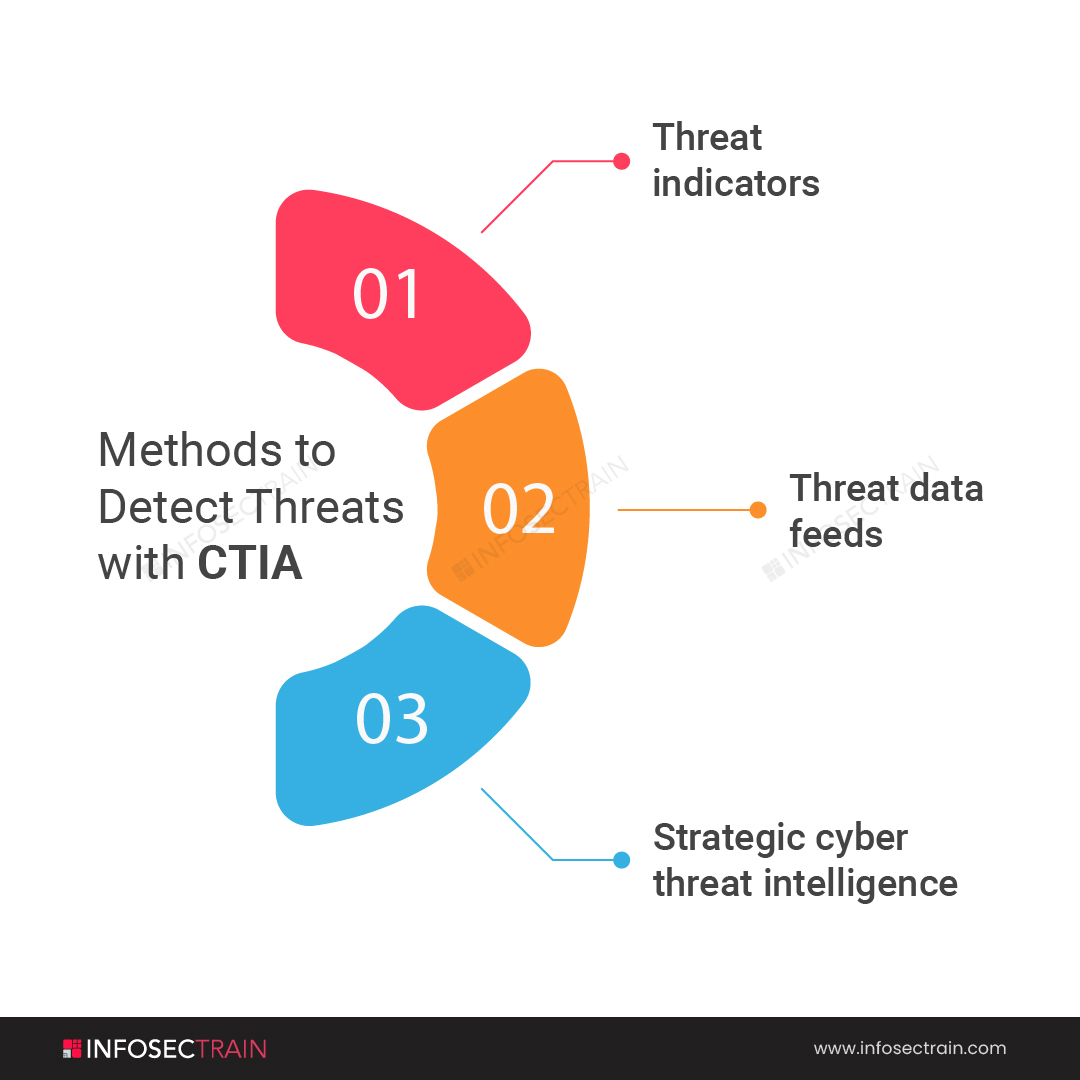
1. Threat Indicators: A threat Indicator is also called an indicator of compromise, is an entity that is used to alter the system if there are any possibilities of an attack. The most common types are IP addresses, reputation data on the domain, and file signatures that have been connected with the attack.
A malware file signature is a unique identifier of a particular worm, trojan virus, or any different kind of code. A file that contains malware will frequently run on MD5 or SHA-1 algorithms. This algorithm generates a unique fingerprint based on a series of bytes. That unique fingerprint will look something like this:
55fsjj85322hstel55knar79lk63kgeir.
IP address, URLs, and Domains reputations are risk ratings of web pages and computers over the internet. High-risk rates are attached with the systems or websites connected with:
- Spam
- Malware
- The IP addresses that are darknetted
- Data exfiltration services
2. Threat data feeds: Threat data feeds give information that associates and analyzes threat indicators. Threat data feeds help the security teams to recognize the patterns associated with attacks. It also helps the incident response teams understand the malware files’ behavior to respond to the threats quickly.
Threat data feed includes Cyber threats statistics and surveys.
Statistics:
Organizations, industries, and cybersecurity vendors offer statistics on malware, bonnets, spams, and other elements of cyberattacks.
Surveys and Reports:
Reports are based on the different aspects of cybersecurity and cyber threats. These reports include:
- Statistics on various types of attacks
- Expert analysis
- Results of a survey
Survey data is essential because it gives information about organizations’ success, failures, and overall experiences in responding to threats.
3. Strategic Cyber Threat Intelligence:
Strategic Cyber Threat Intelligence is data regarding respective rivals that are targeting your organization. Cyber Threat intelligence also gives information regarding the dangers that are associated with the enemies.
The cybercriminals and hackers that we are discussing have created a complete underground universe where participants:
- Exchange ideas about the tools and tactics to successfully attack the systems.
- To share the knowledge on how to create and use malware.
- Hackers can buy and sell the tools required to attack.
- Offers services to other hacktivists ranging from some specialized tasks to outsourcing complex activities
- Buy and sell digital assets like social security numbers, login credentials, credit card numbers, and other personal information.
CTIA with InfosecTrain:
InfoSecTrain is one of the best globally recognized companies that focuses on Information security services and IT security training. Enroll in our CTIA certification and training course to experience the practical sessions and excellent training from the best trainers.



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
