Domain 1 of CEH v11: Information Security and Ethical Hacking
A CEH (Certified Ethical Hacker) is a professional who typically works within a Red Team environment. A Certified Ethical Hacker’s focus must be on attacking systems and accessing applications, networks, databases, or other crucial data on the secured systems. In addition to recognizing attack strategies and exploiting creative attack vectors, a CEH can mimic the skills and creativity of malicious hackers. Unlike black hat hackers, certified ethical hackers approach systems with permission from their owners and maintain the confidentiality of their work.

The job opportunities for a Certified Ethical Hacker are very high because of the increasing cybercrimes. If you are interested in learning CEH, this blog is for you. In this blog, you will get to know about all the domains of CEH certification. Let’s dive into the topic.
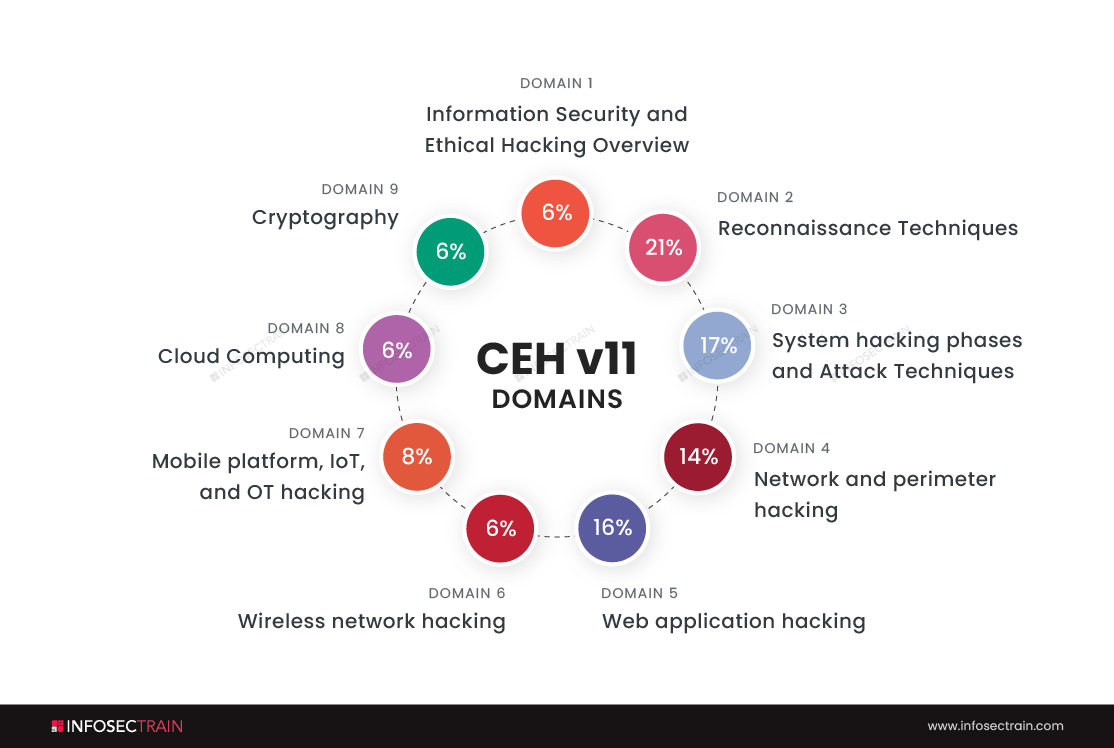
Domains of CEH:
- Information Security and Ethical Hacking Overview-6%
- Reconnaissance Techniques-21%
- System hacking phases and Attack Techniques-17%
- Network and perimeter hacking-14%
- Web application hacking-16%
- Wireless network hacking-6%
- Mobile platform, IoT, and OT hacking-8%
- Cloud Computing-6%
- Cryptography-6%
Domain 1: Information Security and Ethical Hacking Overview-6%
The process of hacking involves finding vulnerabilities within a computer system. In addition to stealing sensitive information, they can delete files and perform other malicious activities using these vulnerabilities. It is illegal to hack into computers, so you may face sanctions and be imprisoned for years and years if caught. Nevertheless, hacking is legal when conducted with permission. Usually, hackers are hired by owners of organisations to penetrate their systems to discover vulnerabilities so that they can be remedied. Such people who have access to your systems without any malicious intent are called Ethical Hackers, and the process is called Ethical Hacking.
The importance of ethical hacking
The fundamental goal of an ethical hacker is to prevent sensitive data and information from getting into the hands of cyber violators. It protects your organisation from being threatened with extortion by individuals looking to take advantage of the weaknesses.
The advantages of ethical hacking:
- Organisations can find security flaws from an attacker’s point of view to strengthen defenses.
- We can implement a secure network that blocks security violations.
- Ethical hackers can defend national security by preventing terrorists from gaining access to sensitive information.
- We can gain the confidence of our consumers and investors by providing secure products and data.
Types of ethical hacking:
Since virtually any system component may be hacked, there are several ethical hacking methods that need an in-depth understanding of that component. Below you’ll find a list of several ethical hacking techniques.
- Web application hacking: Web hacking refers to the exploitation of HTTP applications by altering the application’s graphical web interface, tampering with the Uniform Resource Identifier (URI), or modifying HTTP components not present in the URI.
- Social Engineering techniques: In social engineering, the goal is to manipulate others into disclosing sensitive information. Criminals employ social engineering techniques because it is far easier to take advantage of your inherent tendency to trust others than it is to figure out how to hack your program or system.
- System hacking: As a result of the penetration of computer systems and software, system hacking allows the hacker to get control of the target machine and steal or misuse the data on it. A malevolent hacker takes advantage of the flaws in a computer system or network to get access to its data or benefit illegally.
- Hacking wireless networks: A wireless network is a collection of two or more devices connected by radio waves within a restricted spatial range. Because wireless networks use radio waves to communicate, an intruder may simply sniff the network from a nearby place. Sniffing the network for SSID is a common attack technique used by hackers.
- Web server hacking: A server-side software program generates web content in real-time. Hackers use DoS (DDoS) assaults, SYN floods, ping floods, port scans, sniffer attacks, and social engineering to steal credentials, passwords, and corporate information from the web server.
Job opportunities you get as an Ethical Hacker:
- Information Security Analyst
- Security Analyst
- Certified Ethical Hacker (CEH)
- Ethical Hacker
- Security Consultant(Computing/Networking/Information Technology)
- Information Security Manager
- Penetration Tester
CEH with InfosecTrain:
InfosecTrain is one of the leading training providers with a pocket-friendly budget. We invite you to join us for an unforgettable journey with industry experts to gain a better understanding of the Certified Ethical Hacker course. Courses can be taken as live instructor-led sessions or as self-paced courses, allowing you to complete your training journey at your convenience.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
