Domain 3 of CEH v11: System Hacking Phases and Attack Techniques

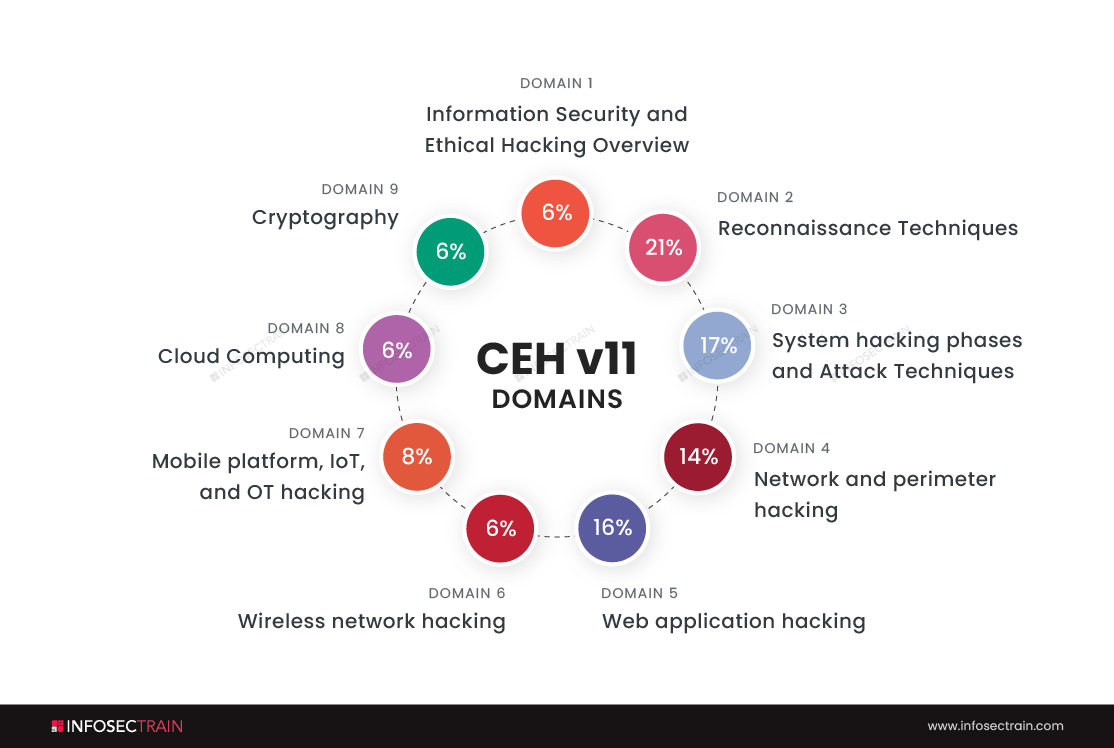
Domains of CEH
- Information Security and Ethical Hacking Overview-6%
- Reconnaissance Techniques-21%
- System hacking phases and Attack Techniques-17%
- Network and perimeter hacking-14%
- Web application hacking-16%
- Wireless network hacking-6%
- Mobile platform, IoT, and OT hacking-8%
- Cloud Computing-6%
- Cryptography-6%
Hacking is a dangerous process that hackers use to gain unauthorized access to any smartphone, television, computer, or other network system. The hackers constantly update their programming and computer skills to enter the target’s system without the target’s knowledge and gain valuable financial and personal information.
Not every hacker wants to exploit your system and get unauthorized access. Some of them utilize their skills to protect your confidential data, and they are called ethical hackers. In this blog, We will discuss the third domain of CEH, which is ‘system hacking phases and attack techniques’, where you will witness the hacking phases and techniques used by both malicious hackers and ethical hackers. Infact, both use the same techniques and phases but with different intentions.
System hacking phases
The six hacking phases are:
- Reconnaissance
- Scanning and enumeration
- Gaining access
- Ascendancy of privileges
- Maintaining access
- Track coverage
Reconnaissance: Reconnaissance is the first and pre-phase of hacking. Reconnaissance is the process of gathering all the information about the target system, like active ports, operating systems, and all the passive information.
For example, assume you want to surprise your childhood friend who lost touch with you. The first thing you will do is gather all the information about them, like their city, area, home address, etc. The process of collecting this information is called reconnaissance.
Scanning and enumeration:
This scanning and enumeration phase is where the attacker moves from passive to active information gathering. The scanning is performed to gain access to the target system, and the enumeration is performed to get detailed information, including the user account data.
There are three types of scanning.
- Port scanning: Port scanning is a phase where hackers scan the target system for data like live systems, open ports, and different services running over the host.
- Network mapping: A network map depicts a network’s topology, routers, firewalls, servers, if any, and host information. During the hacking process, this network map can be a valuable source of information.
- Vulnerability scanning: The vulnerability scanning process involves scanning the target for weaknesses or vulnerabilities that could be exploited. This kind of scanning is usually done with automated tools.
Gaining access: Gaining access is one of the important phases of hacking any system/network. This is the phase where the attacker moves from simply examining the network to actually attacking it. Hackers can gain access by using various methodologies, like identifying a wireless access point or by identifying vulnerabilities within the web server software.
Ultimately, a hacker’s method of accessing a network will depend on his skills, how much access he gains, and how the victim’s network is configured.
Privileges ascendancy: Even though the hacker has got access to the network or your system, he tries to escalate his privileges to an administrator because they are the individuals who control the whole network.
In simple terms, privilege escalation can be described as exploiting a bug or vulnerability in an application or operating system to gain access to resources that would otherwise be protected from an average user.
Maintaining the access: Hackers have to maintain access to complete their tasks successfully. This can be done by using rootkits, trojans, and various other malicious files.
Track coverage: No one wants to get caught after doing a robbery. Hence, the hackers cover all their tracks so that the network/system owner will never know who attacked the network/system. A good hacker will cover or clear his tracks by changing the registry values and removing/changing/corrupting the log values.
Different attacking techniques used by a hacker
Bait and Switch: Bait and Switch is a process where a hacker buys advertising space on any website, and he posts a very interesting ad that attracts users to click on it. Once the user clicks that ad, it will immediately redirect him to a malicious page, and from there, a hacker can install bugs and malicious codes into your system. So guys, be very careful whenever you are clicking an ad.
Cookie Theft: I think this is a dangerous attack because we save many passwords in our browsers, say our email passwords, bank accounts, or many important accounts. Once the attacker gets your cookie session, he can replicate you and conduct attacks or simply steal that information. So, make sure you regularly clear your search history and cache.
Installing various trojans and malware like trojan and spyware: A hacker installs various malware on a target’s computer. These trojans and spyware frequently send the data to the attacker and perform few tasks like diverting traffic and sniffing the victim’s data.
CEH with InfosecTrain
InfosecTrain is one of the leading training providers with a pocket-friendly budget. We invite you to join us for an unforgettable journey with industry experts to gain a better understanding of the Certified Ethical Hacker course. Courses can be taken as live instructor-led sessions or as self-paced courses, allowing you to complete your training journey at your convenience.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
