Let’s Discuss Threat Modeling: Process & Methodologies
In today’s digital era, almost all IT systems are vulnerable to several threats, and as technology advances, more are being added all the time. These threats might originate from the outside or within an organization, and their consequences can be disastrous. Systems could be rendered inoperable or sensitive data could be exposed, lowering consumer confidence in the system’s supplier. Organizations can use threat modeling techniques to think defensively to prevent these threats from exploiting system weaknesses. This article will discuss the threat modeling process and its various methodologies.

Introduction to threat modeling
Threat modeling is a method for assessing an application’s or system’s security. It is a method used to identify, quantify, and mitigate the security risks connected with an application or system. Threat modeling’s goal is to offer defenders a systematic analysis of what controls or defenses are required, given the system’s structure, the likely attacker’s profile, the most probable attack vectors, and the assets most desired by an attacker.
You might have juggled with various questions every day like:
- What areas of my business are the most vulnerable to attack?
- What are the most pressing risks?
- What should I do to safeguard my organization from these cyber attacks?
Threat modeling provides answers to all of these questions and hence helps in the prevention of potential attacks.
When is it appropriate to use threat modeling?
Threat modeling must be done early in the development cycle to identify and address any vulnerabilities early on, avoiding a far more expensive fix later. Considering security requirements through threat modeling can lead to proactive architectural decisions that help decrease threats from the start. Aside from that, it is vital to keep the threat model updated. A threat model review and an update should be performed whenever an application, linked technologies, or the threat landscape changes.
How does the threat modeling process work in general?
Threat modeling entails identifying possible or actual vulnerabilities and implementing countermeasures and controls to ensure that these vulnerabilities are not exploited, which results in data loss for an organization’s IT systems. It will handle the actual implementation of the solutions to assist in loss prevention with caution.
We can use a variety of approaches when it comes to threat modeling. One method is to look at it from the attacker’s point of view. Let’s say we have an internet attacker. This attacker could come from the outside or from within the network. From their perspective, we can focus on an attacker’s goals and abilities in terms of what they can accomplish with our data and systems.
Another option is to approach it from the standpoint of architecture. Servers, switches, firewalls, routers, printers, infrastructure, and data are all present. And we can look at each of them from an architectural standpoint, identifying individual vulnerabilities that may be linked to each of these different components and then implementing countermeasures to defend those vulnerabilities from attackers.
The third general approach focuses on the assets, such as essential data in every system component. The point of this approach is to identify crucial assets that would have a significant impact on corporate operations if they were compromised or made unavailable. It determines the motivation of possible attackers to gain access to these resources, as well as the value of these resources to the attacker and the amount of work required to compromise these assets. We tackle the threats from all three perspectives in most organizations.
The threat modeling process includes a number of steps.

Why do organizations need security threat modeling?
Threat modeling helps organizations to:
- Identify and respond to the most severe security risks
- Eliminate security concerns during the design phase
- Prepare mitigation strategies for threats that have been recognized and documented
- In a cost-effective approach, improve the security posture of your organization
- Make logical security decisions
What are the threat modeling methodologies?
There are various structured threat modeling methodologies or frameworks. A few of them are:
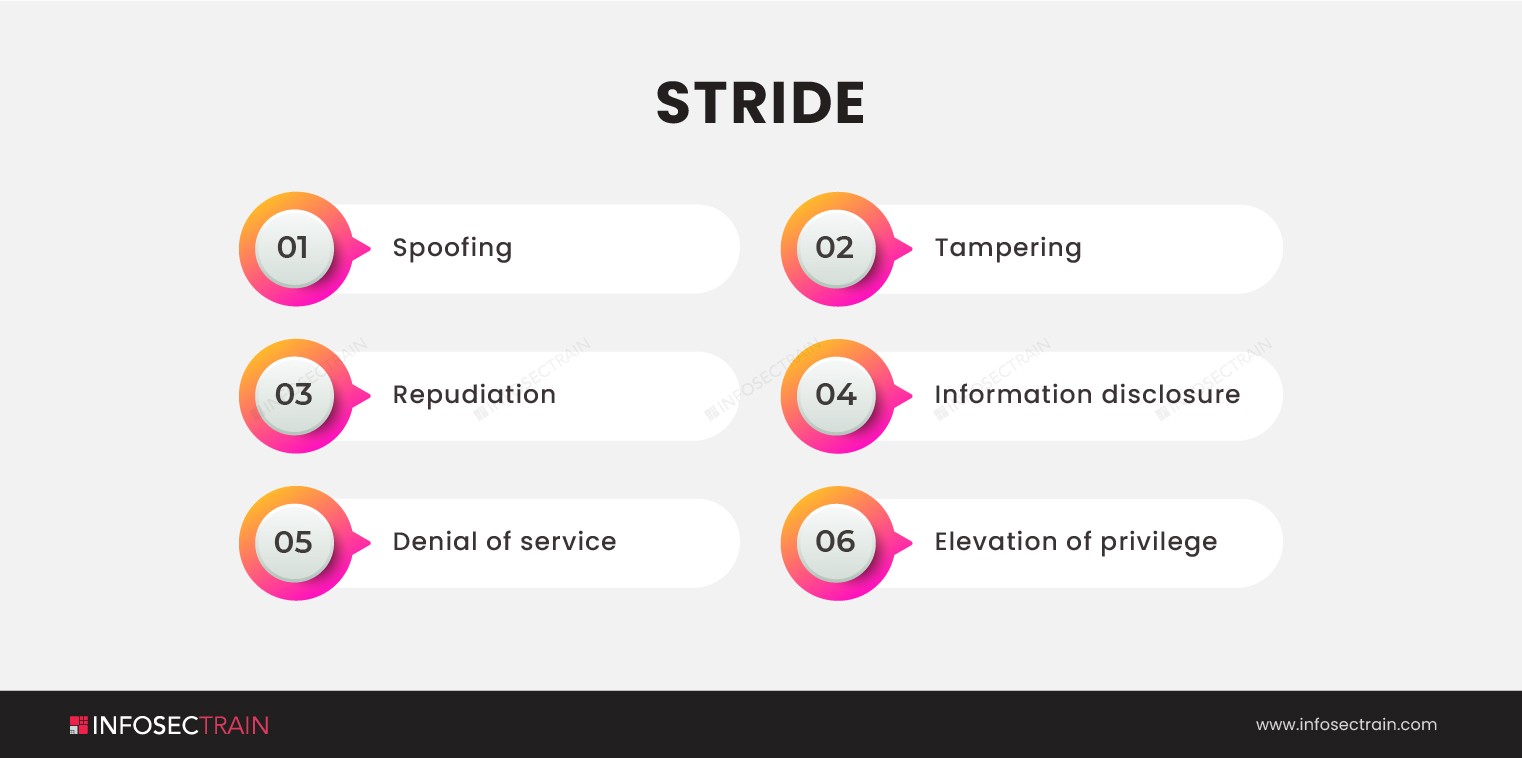
STRIDE: STRIDE is the exceptional threat modeling method currently available, which is an application-centric approach. It was developed by Microsoft. IT security teams can use the STRIDE threat model to identify threats and vulnerabilities during the design process of an application or system. It aims to ensure that an application or system meets the CIA triad. STRIDE is an acronym for six different types of threats. These are:
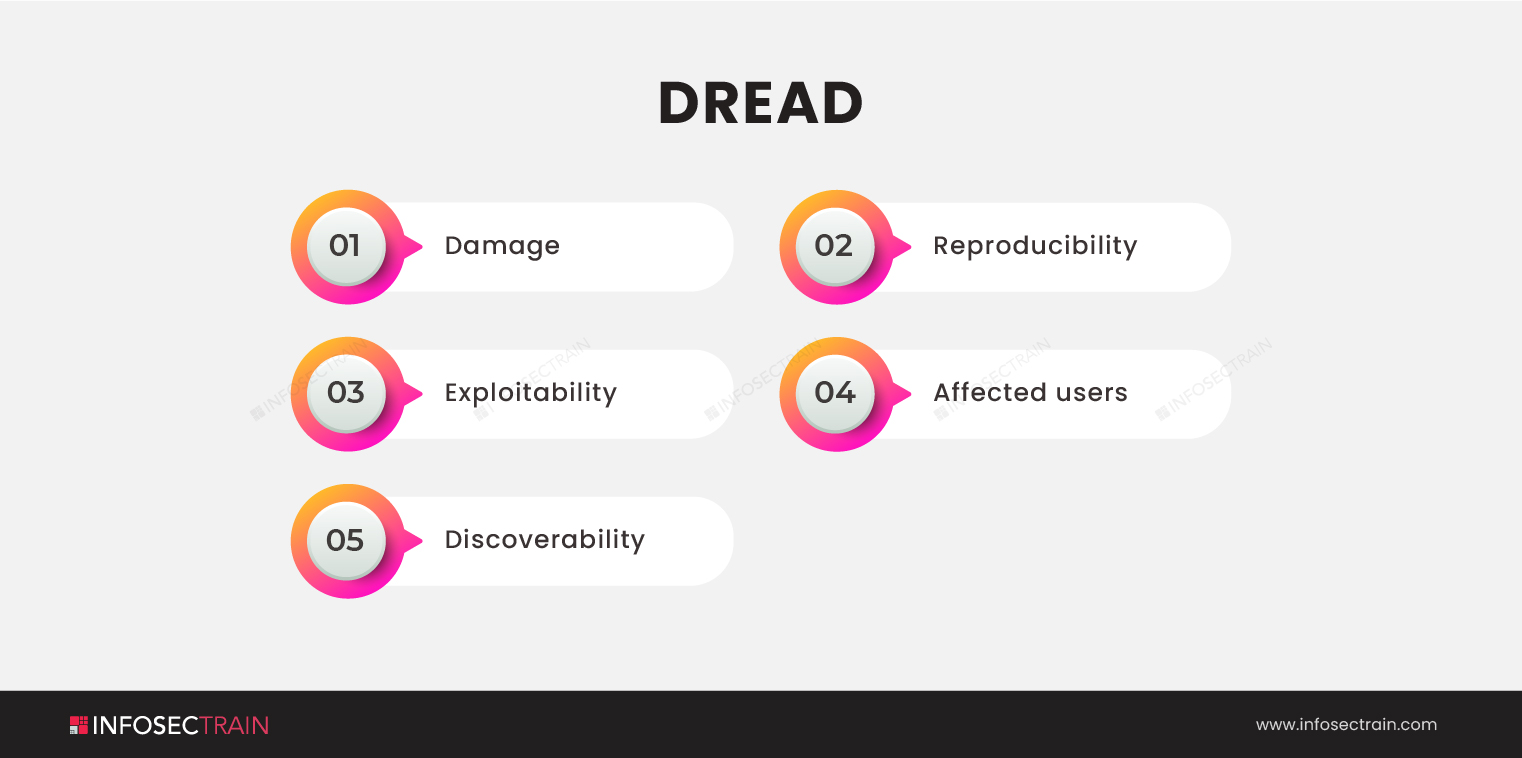
DREAD: DREAD is a component of a system used for analyzing the risk of IT security threats. It was proposed for threat modeling; however, Microsoft discontinued it in 2008 due to mixed reviews. It is used by OpenStack and other businesses now. DREAD uses five categories to give a mnemonic for risk evaluating security threats. These are:
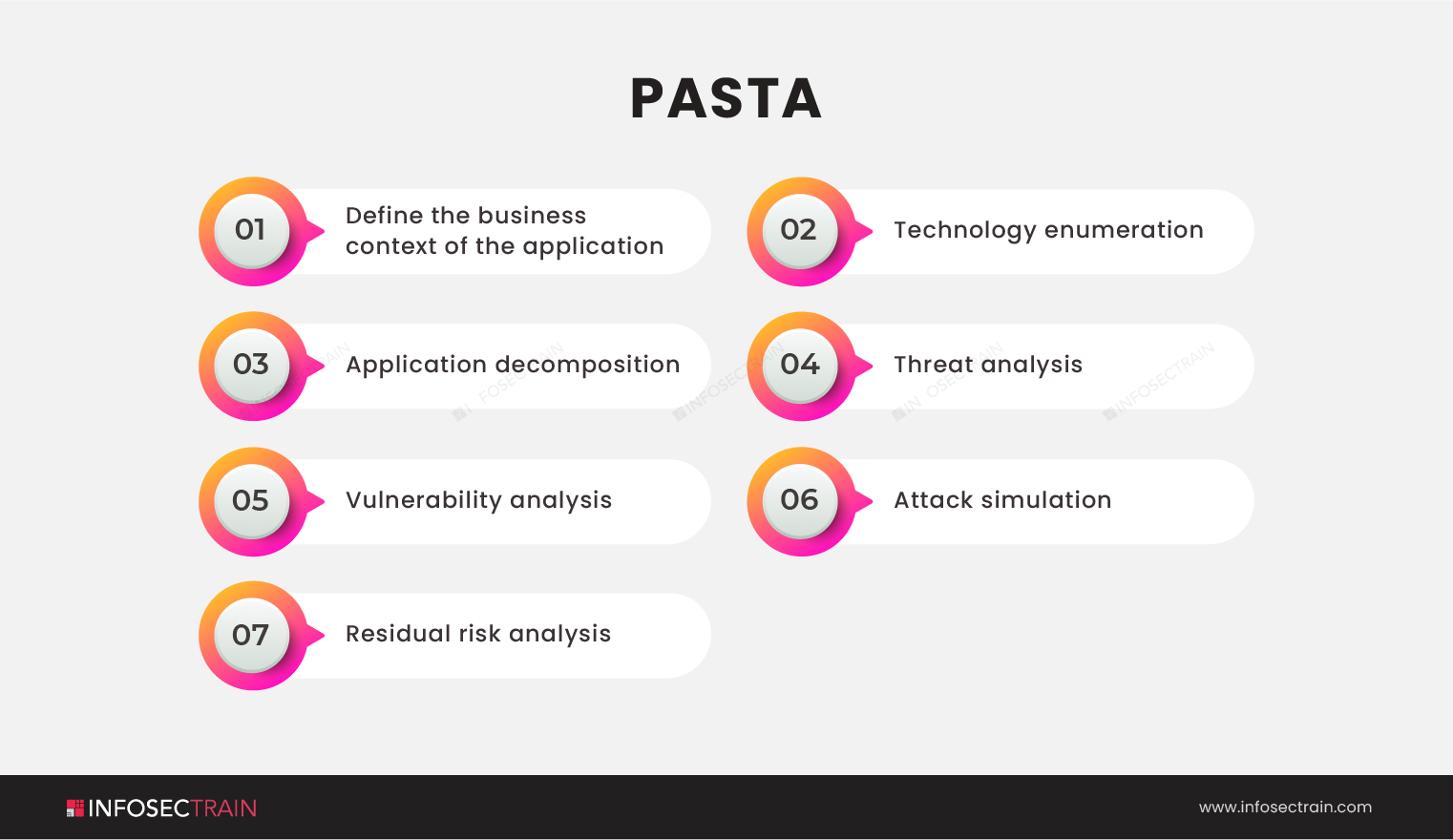
PASTA: PASTA or the Process for Attack Simulation and Threat Analysis is a risk-centric approach. It combines an attacker’s perspective of a business with risk and impacts analysis to generate an overall picture of the risks to components and applications, their vulnerability to attack, and influencing risk and priority decisions for solutions. Most application threat models did not even consider actual threats before the PASTA threat model. It is a seven-step methodology. They are:
Trike: Trike is a risk-based threat modeling approach with a unique implementation and risk modeling process. The trike is a one-of-a-kind open source threat modeling process aimed to complete the security audit process from the perspective of cyber risk management. Its foundation is a requirement model.
Attack Tree: One of the oldest and most extensively used strategies for modeling threats on IT systems is the use of attack trees. It gives a formal and systematic approach to express the security of systems based on various attacks. In simple terms, they are diagrams that illustrate attacks on a system in the structure of a tree.
CVSS: The Common Vulnerability Scoring System abbreviated as CVSS, is a technique to encapsulate the critical characteristics of a vulnerability and generate a numeral score that reflects its severity.
VAST: VAST stands for Visual, Agile, and Simple Threat Modeling. VAST was generated to integrate into developers’ and application architects’ workflows. It is based on ThreatModeler. ThreatModeler is an automated threat modeling tool that discriminates between application and operational threat models.
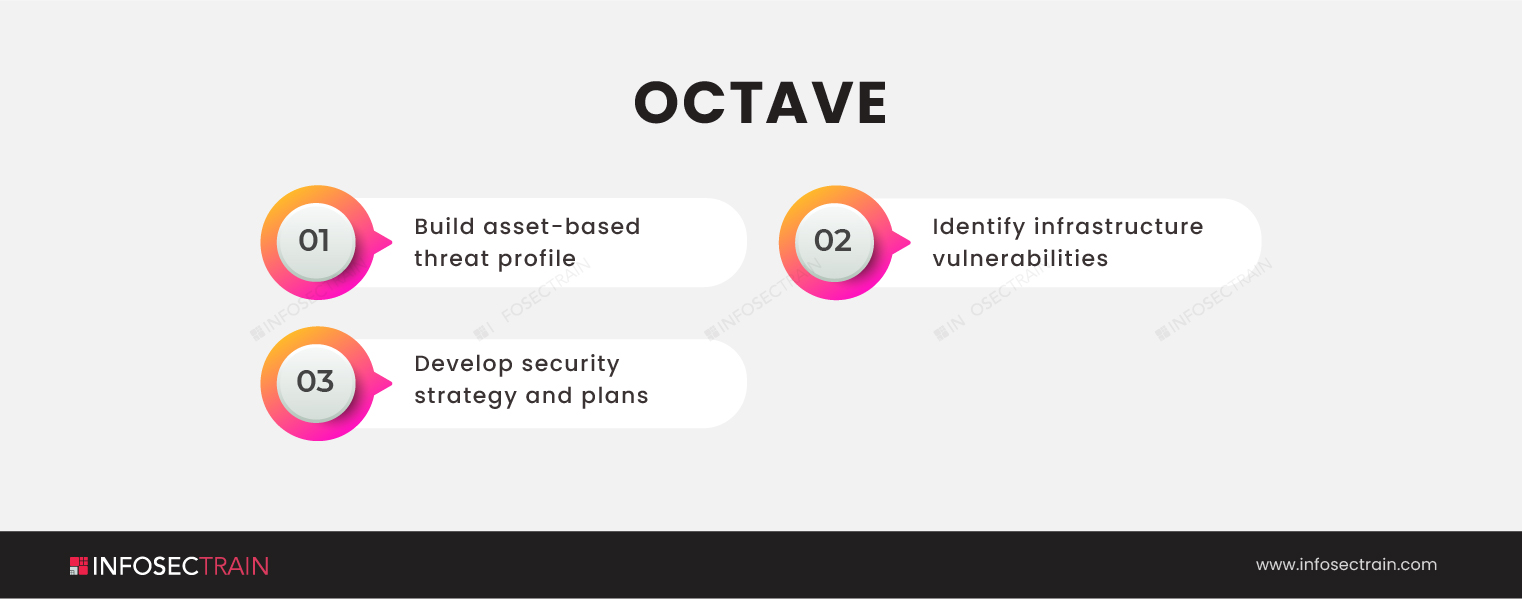
OCTAVE: The Operationally Critical Threat, Asset, and Vulnerability Evaluation or OCTAVE methodology is a risk-based strategy for tactical cybersecurity evaluation and planning. It focuses on evaluating the risks to an organization’s information assets due to a data breach. It has three phases. They are:
How can a threat model be created?
The formation of a visual representation of the application and infrastructure that is assessed is the first step in any IT-related threat modeling process. Two methods can do it:
- Visual representation using data flow diagrams
- Visual representation using a process flow diagram
Tools for threat modeling
One can use threat modeling tools to detect and resolve possible security threats to your program, data, or device ahead of time. One may rest assured that half the battle is achieved when they use these tools. A few of the tools that can be used for the threat modeling are:
- OWASP Threat Dragon
- ThreatModeler
- Cairis
- IriusRisk
- Microsoft Threat Modeling Tool
- VM
Final words
Cybercriminals would love to glean the data held by almost every firm. It is essential to have a clear and complete picture of everything that needs to be protected and be aware of all the numerous angles an attacker might attack to keep this data safe. This is when a threat model comes to the rescue. Threat modeling can assist you in making your IT systems more secure and reliable. Security in a modern digital business environment without threat modeling is a gamble, and you will certainly lose. InfosecTrain understands this need, and here we provide various security training programs to help you understand the threat modeling process in depth.



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
