Phases of Ethical Hacking
Ethical hackers are highly needed today by businesses and government entities to tackle the growing threat to IT security. Many government organizations, experts, and companies increasingly understand that closing your doors is not enough to defend a system.

Table of Contents
What is Ethical Hacking?
The Advantages of Ethical Hacking
Types of Ethical Hacking
Phases of Ethical Hacking
As more firms seek into the digital realm, protecting data from hackers and cyber-attacks is more crucial than ever. Organizations are now recognizing the potential consequences of these attacks and considering preventative measures, one of which is ethical hacking.
What is Ethical Hacking?
Ethical hacking detects vulnerabilities and carefully addresses them before they worsen. The word permission is used in the hacking process, which separates ethical hacking from other hacking tactics.
Ethical hacking is the analysis of an organization’s security strategy by a team of professionals known as “White hat hackers or Red Team Experts.” Their primary goal is to compromise the system to address the vulnerability with explicit permission from the organization and to deliver a performance measurement system showing the possibility of risk. Public and commercial companies, as well as banks, usually employ ethical hackers to combat cybercrime.
The Advantages of Ethical Hacking
The main advantage of ethical hacking is to restrict illegal adversaries from stealing and misusing data, as well as:
- Finding weaknesses from an attacker’s perspective so that vulnerabilities are addressed
- To prevent network security breaches, implement a strong and secure network
- Enhancing consumer’s and shareholder’s trust by maintaining the security of their services and data
- Assisting in network protection with real-world evaluations
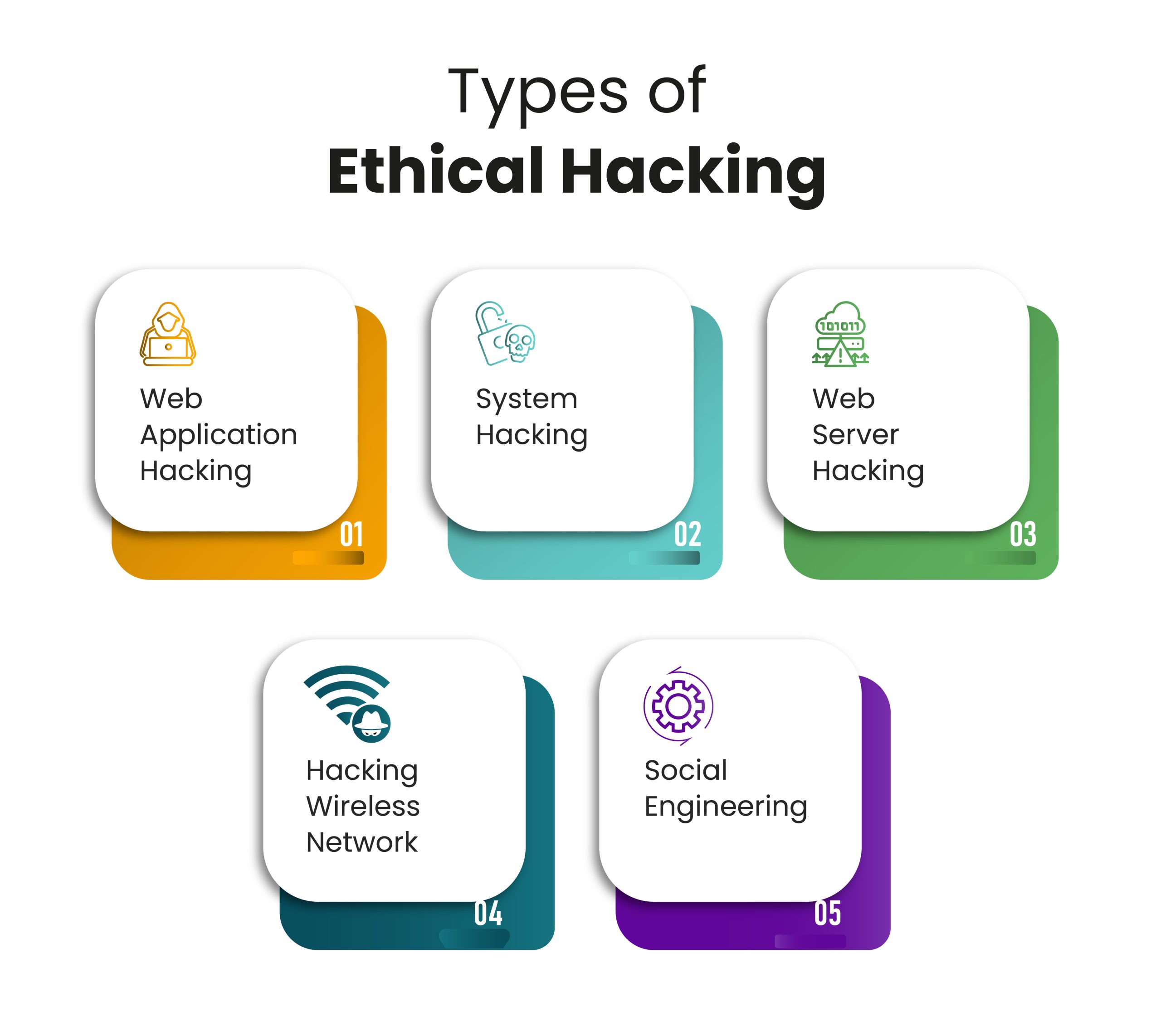
Types of Ethical Hacking
Undoubtedly, every organization, network, website, equipment, etc., may be stolen. Ethical hackers must learn to think like malicious hackers and be familiar with the tools and strategies they are likely to employ to comprehend how the hack might occur and the impact. Here are the common types of ethical hacking, which include:
Phases of Ethical Hacking
Organizations recruit ethical hackers to replicate an actual cyberattack on their systems and networks. This attack consists of several phases, and it requires a ton of expertise and works for ethical hackers to discover all vulnerabilities and leverage them properly.
This hypothetical attack is designed to highlight all weak areas in the enterprise and attempt to address them. The five phases of ethical hacking are as follows:
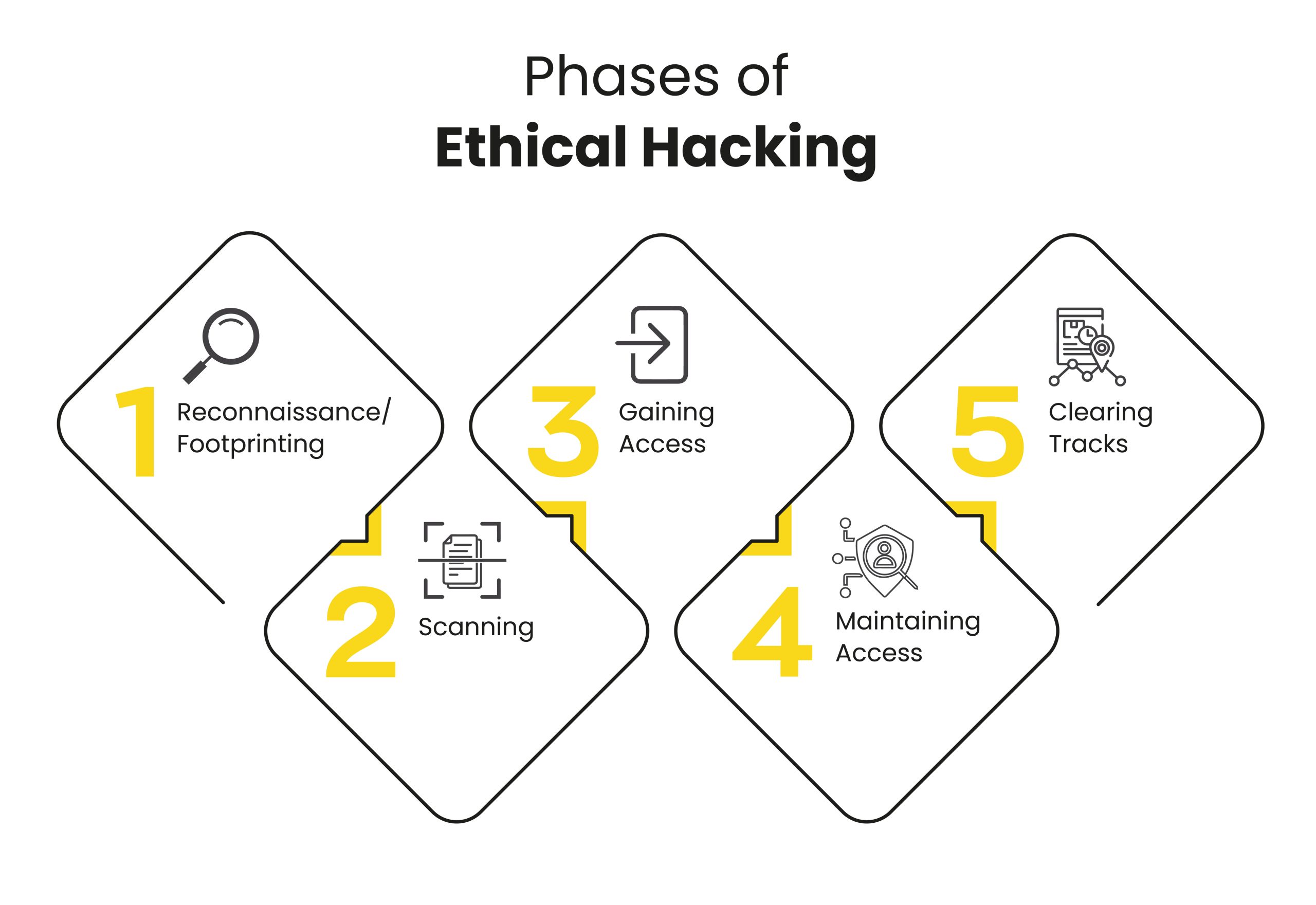
1. Reconnaissance/Footprinting
Reconnaissance is the first phase of ethical hacking, also known as the footprinting and information gathering phase. This is the preliminary phase where white hat hackers gather as much information as possible and implement security measures into the targeted system or network. The information gathered by white hat hackers usually is about three groups: network, host, and people. There are mainly two types of footprinting:
- Active footprinting: Communicate with the target directly to gather information about the target.
- Passive footprinting: Seeking to get information about the target without gaining direct access to the target. Hackers exploit social media, public websites, and other public resources.
2. Scanning
The scanning phase is the second step in an ethical hacker’s methodology. It entails applying all the knowledge learned during the reconnaissance phase to the target location to search for vulnerabilities. Hackers search for data such as user accounts, credentials, IP addresses, etc. There are three types of scanning, which include:
- Port scanning: During this stage, the target is scanned for data such as open ports, live systems, and other services active on the host.
- Vulnerability scanning: This scanning technique identifies a target’s vulnerabilities and weak points and attempts to exploit those bugs in various ways. It is carried out using automated tools such as Netsparker, OpenVAS, Nmap, and others.
- Network scanning: This method includes locating the organization’s firewall and other routers and networks to assist them in their hacking operations.
3. Gaining Access
In this phase, the hacker creates the blueprint for the target’s network using the data gathered in Phases 1 and 2. Now the hacker has all of the information he requires. So he creates the network map and decides how to carry out the attack? There are various alternatives, such as:
- Phishing attacks
- Brute force attack
- Spoofing attack
- Man in the middle attack
- Dos attack
- Session hijacking
- Buffer overflow attacks
The hacker obtains access to the network, programs, and system and then extends their access permissions to manage connected systems.
4. Maintaining Access
When a hacker gains access, they choose to maintain it for future exploitation and attack. In addition, the hacker gains access to the organization’s Rootkits and Trojans and utilizes them to execute more network attacks. An ethical hacker attempts to keep access to the target until they have completed the activities or intend to complete in that target.
5. Clearing Tracks
Once a hacker has obtained access, they leave no trace to prevent detection by the security team. They execute this by deleting cache and cookies, interfering with log files, and closing all open ports. This incorporates some of the steps an ethical hacker uses to cover and eliminate their footprint.
- Deleting/corrupting all logs
- Changing the values of logs or registries
- Removing all of the folders established by the ethical hacker
- Uninstalling all the applications
Ethical hackers use the following methods to hide their tracks in ethical hacking:
- Using reverse HTTP shell
- Tunneling with ICMP (Internet Control Message Protocol)
CEH v11 with InfosecTrain
The process of ethical hacking is prolonged, challenging, and includes multiple phases. Working professionals must have extensive knowledge and relevant security certifications to succeed as ethical hackers. You can pursue an ethical hacking certification to learn more about evaluating and enhancing security procedures and network architecture. A person can take the Certified Ethical Hacking (CEH v11) training offered by InfosecTrain to comprehend and use hacking tools and techniques to hack into an organization properly.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
