Top Tools Covered in CEH v12

Ethical hacking is the process of finding weaknesses and security flaws in systems and programs by impersonating the reasons and activities of cybercriminals. Ethical hacking tools are just computer scripts and programs that help professionals find and take advantage of vulnerabilities in computer systems, networks, and web apps.
Table of Contents
What are Hacking Tools?
Top CEH v12 Tools
Reconnaissance/Footprinting Tools
Scanning Tools
Gaining Access Tools
Maintaining Access Tools
Clearing Tracks Tools
Other Miscellaneous Tools
What are Hacking Tools?
The software and techniques used by hackers to discover vulnerabilities in IT system’s operating systems, various web applications, servers, and networks are nothing more than computer programs or a sophisticated form of script created by developers. These days, many organizations use ethical hacking methods to protect their data from intruders. Ethical hacking tools can be purchased or downloaded in open source or commercial solutions.
Top CEH v12 Tools
This article tries to be more than just a list of all tools as they appear in the CEH v12, but also to organize them according to the phase of hacking to which they would belong. According to CEH v12, the phases of ethical hacking are as follows:
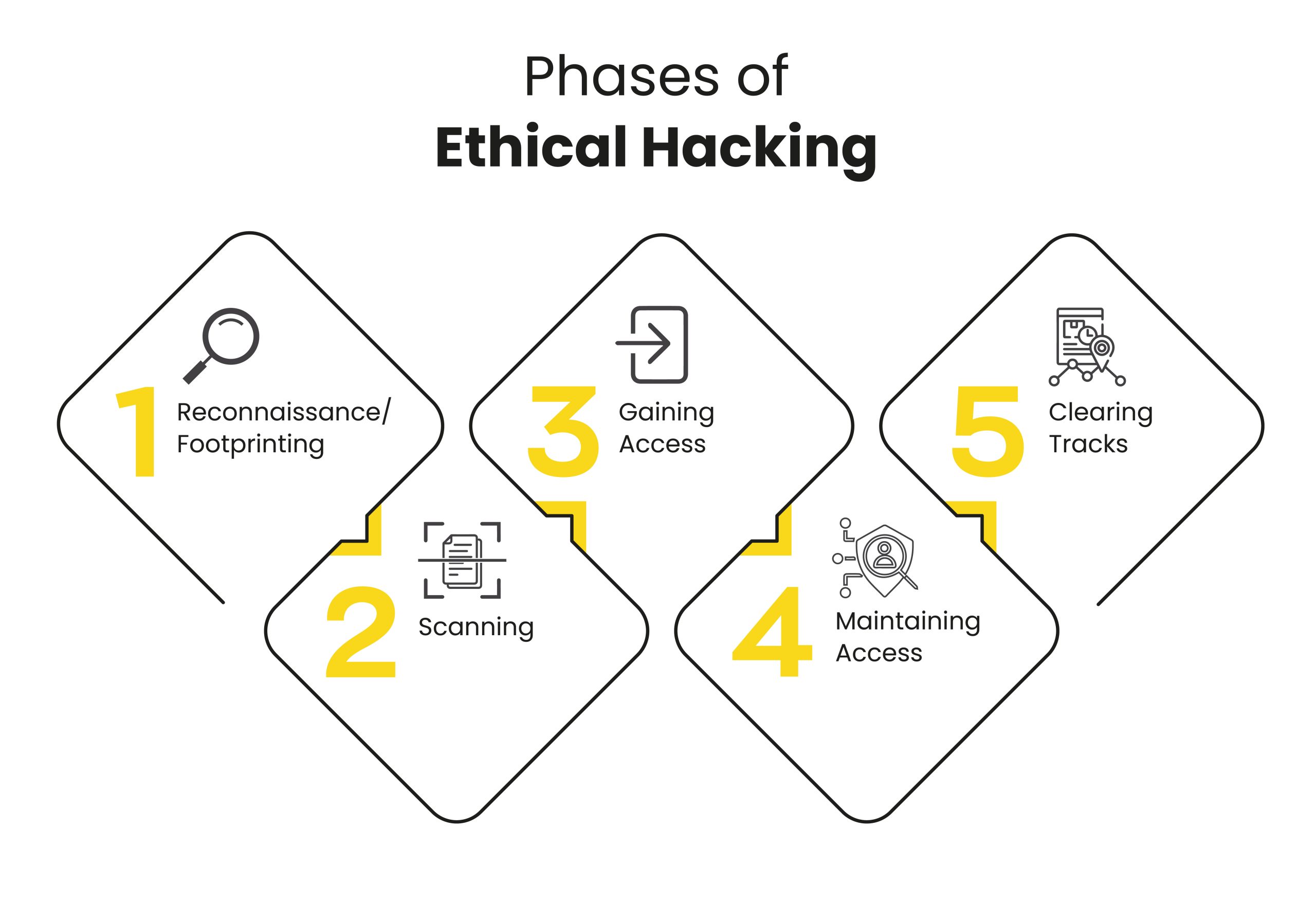
1. Reconnaissance/Footprinting Tools
Reconnaissance, often known as the footprinting or information gathering phase, is the initial phase of ethical hacking. This is the preliminary phase, where white hat hackers acquire as much data or information as possible and deploy security protocols into the intended system or network. In this phase, different kinds of tools are used to gather information. So here are the reconnaissance/footprinting tools:
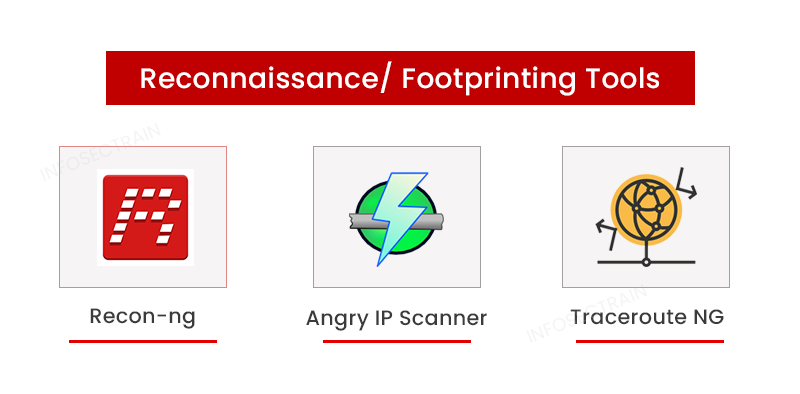
- Recon-ng: Recon-ng is a full-featured reconnaissance tool that aims to provide a robust environment for doing open-source, web-based reconnaissance rapidly and thoroughly.
- Angry IP Scanner: This free tool scans ports and IP addresses. This scanner supports Windows, macOS, and Linux and may be used on the Internet or your local network.
- Traceroute NG: Traceroute is a network path analysis tool. It can identify host names, packet loss, and IP addresses and provide reliable analysis through a command line interface.
2. Scanning Tools
The second step in ethical hacking is the scanning phase. It comprises going to the target place and using all the information gathered during the reconnaissance phase to look for vulnerabilities. So tools used for the scanning phase are:
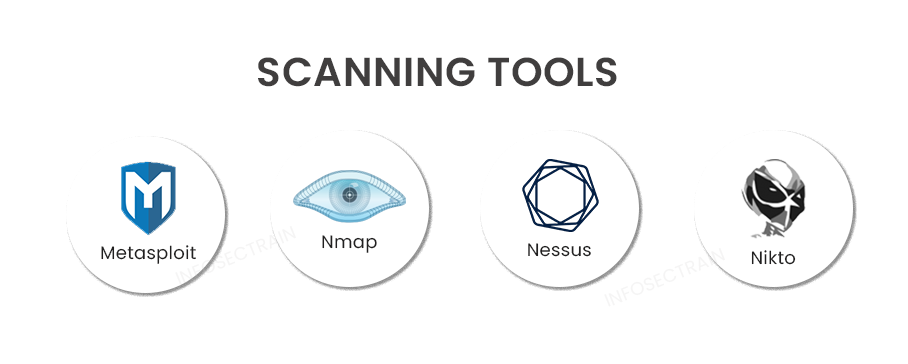
- Metasploit: The Metasploit Framework is free and open source, but Metasploit Pro is a paid product with a 14-day trial. Metasploit is designed for Penetration Testers and Ethical Hackers who can create and exploit codes against remote systems.
- Nmap: Nmap (Network Mapper) is a free network research tool that also functions as a security and port scanner. Both small networks and massive networks can use it. Nmap is a tool that security professionals can use to manage service upgrade schedules, monitor host and service uptime, and inventory networks.
- Nessus: The most well-known vulnerability scanner tool in the world, called Nessus, was created by Tenable Network Security. It is free and mostly suggested for non-business use. This network vulnerability scanner effectively identifies severe flaws in any system.
- Nikto: Nikto is a web scanner tool that checks and tests several web servers to find outdated software, potentially harmful CGIs or files, and other concerns. It can carry out server-specific and generic checks and printing by capturing the received cookies.
3. Gaining Access Tools
Utilizing the information obtained in Phases 1 and 2, the hacker constructs the network’s blueprint at this phase. Tools used in this phase are:

- Aircrack-ng: Wi-Fi security is becoming increasingly crucial as more people utilize wireless networks. Aircrack-ng provides Ethical Hackers with command-line tools for testing and evaluating Wi-Fi network security.
- L0phtcrack: A tool called L0phtCrack is used to audit and recover passwords used on networks to make sure they are hard to crack, frequently changed, and never recovered.
- Ophcrack: A free Windows password cracker based on rainbow tables is called Ophcrack. The method’s creators used a very effective implementation of rainbow tables. It works on different platforms and has features like Graphical User Interface (GUI).
- Hashcat: The fastest and most sophisticated password recovery tool in the world, hashcat supports five different attack methods for over 300 high-performance hashing algorithms. Hashcat contains the tools to support distributed password cracking and currently supports CPUs, GPUs, and other hardware accelerators on Windows, Linux, and macOS. License.
4. Maintaining Access Tools
When a hacker obtains access, they decide to keep it around for potential use and exploitation in the future. The hacker also obtains access to the organization’s rootkits and trojans to carry out additional network attacks. Here are the tools used in this phase:
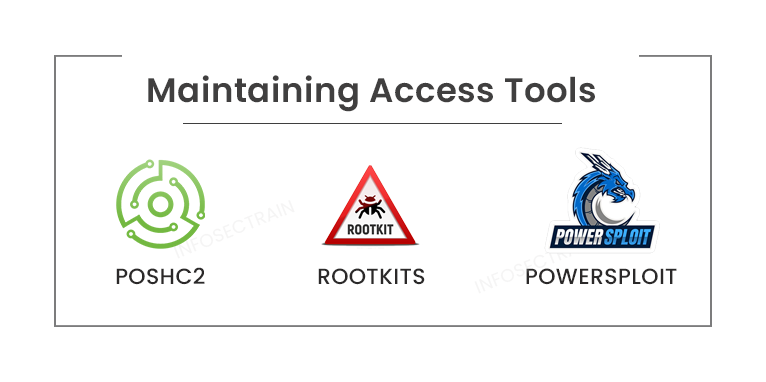
- PoshC2: PoshC2 is mostly built in Python 3 and uses a modular structure to allow users to include their own modules and tools, enabling an extensible and adaptable C2 framework.
- Rootkits: Rootkit tools can intercept and modify common operating system operations. Any information a device reports about itself after being infected by a rootkit is unreliable. Rootkits are all about concealing information.
- PowerSploit: PowerSploit is an open-source offensive security framework with PowerShell components and programs that carry out a variety of penetration testing activities like code execution, persistence, anti-virus evasion, recon, and exfiltration.
5. Clearing Tracks Tools
As soon as a hacker has access, they disappear, avoiding notice by the security team. They interfere with log files, delete cache and cookies, and close all open ports. Here are the tools used in this phase:

- Netcat: The Netcat tool reads and writes data via TCP or UDP network connections. It is meant to be an effective back-end tool that can be used directly or simply driven by other applications and programs. At the same time, it is a powerful network debugging and research tool, as it can make nearly any type of connection, allowing port binding to accept incoming connections.
- Burp Suite: Burp, often known as Burp Suite, is a graphical tool for checking the security of Web applications.
Other Miscellaneous Tools

- Wireshark: Wireshark is an excellent hacking tool for examining data packets and can also undertake in-depth examinations of a wide range of standard protocols. The analysis output can be exported to various file types, including CSV, PostScript, Plaintext, and XML.
- Msfvenom: It is made up of msfpayload and msfencode. It is quick and just uses one instance. Msfvenom includes the standard command-line arguments. We can create payloads for various platforms, including Android, Windows, Unix, Nodejs, Cisco, and others.
- THC Hydra: This tool is a proof-of-concept code that allows hackers and security experts to demonstrate how simple it would be to get unauthorized remote access to a system.
- SQLMap: SQLMap is an open-source tool for penetration testing that automates detecting and exploiting SQL injection problems and acquiring database systems.
CEH v12 with InfosecTrain
The CEH online training and certification program at InfosecTrain adheres to the latest version of CEH v12. The revamped learning framework includes not only a thorough training program to prepare you for the certification exam but also the most robust, in-depth, hands-on lab and practice range experience in the business. So check out InfosecTrain’s CEH v12 certification training program for your ethical hacking learning path.
TRAINING CALENDAR of Upcoming Batches For CEH v12
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 10-Mar-2024 | 27-Apr-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Apr-2024 | 12-May-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 27-Apr-2024 | 02-Jun-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
