How do Phishing and Spoofing Attacks Impact Businesses?
In recent years, prominent organizations and companies have been victims of cybercrime, ranging from data breaches to unlawful access to financial accounts, the digital impersonation of CEOs, and everything in between. From startups to established corporations, businesses of all sizes and industries face security challenges in the digital landscape.

Table of Contents
What is Phishing?
What is Spoofing?
Impact of Phishing and Spoofing Attacks on Businesses
As technology becomes an unavoidable aspect of our lives, the rise of remote work and online ventures opens the door to cybercriminals exploiting IT security risks. In this article, we delve into the profound impact of phishing and spoofing attacks on businesses, highlighting emerging threats and the need for proactive measures to safeguard individuals and organizations.
What is Phishing?
Phishing is an attack in which an attacker attempts to influence an unprepared target to reveal valuable information such as passwords, credit card numbers, and intellectual property. Emails impersonating genuine businesses such as banks, tax offices, and other reputable entities are frequently used in phishing attempts. Phishing is the most well-known type of cyberattack because it is simple to perform and surprisingly powerful.

What is Spoofing?
In terms of cybersecurity, spoofing occurs when someone or something pretends to be someone or something else to gain user trust, obtain access to their systems, steal data, steal money, or spread malware. Spoofing attacks include email spoofing, caller ID spoofing, text message spoofing, IP spoofing, facial spoofing, etc.
Impact of Phishing and Spoofing Attacks on Businesses
Phishing and spoofing are deceitful ways of getting sensitive information by mimicking a reputable entity. A successful cyber-attack can cost any organization a fortune to recover from, and such attacks may leave some organizations unable to recover. Depending on the scope of the operation, the cost of phishing and spoofing attacks might be severe. The following are some of the ways that phishing and spoofing attacks damage businesses:
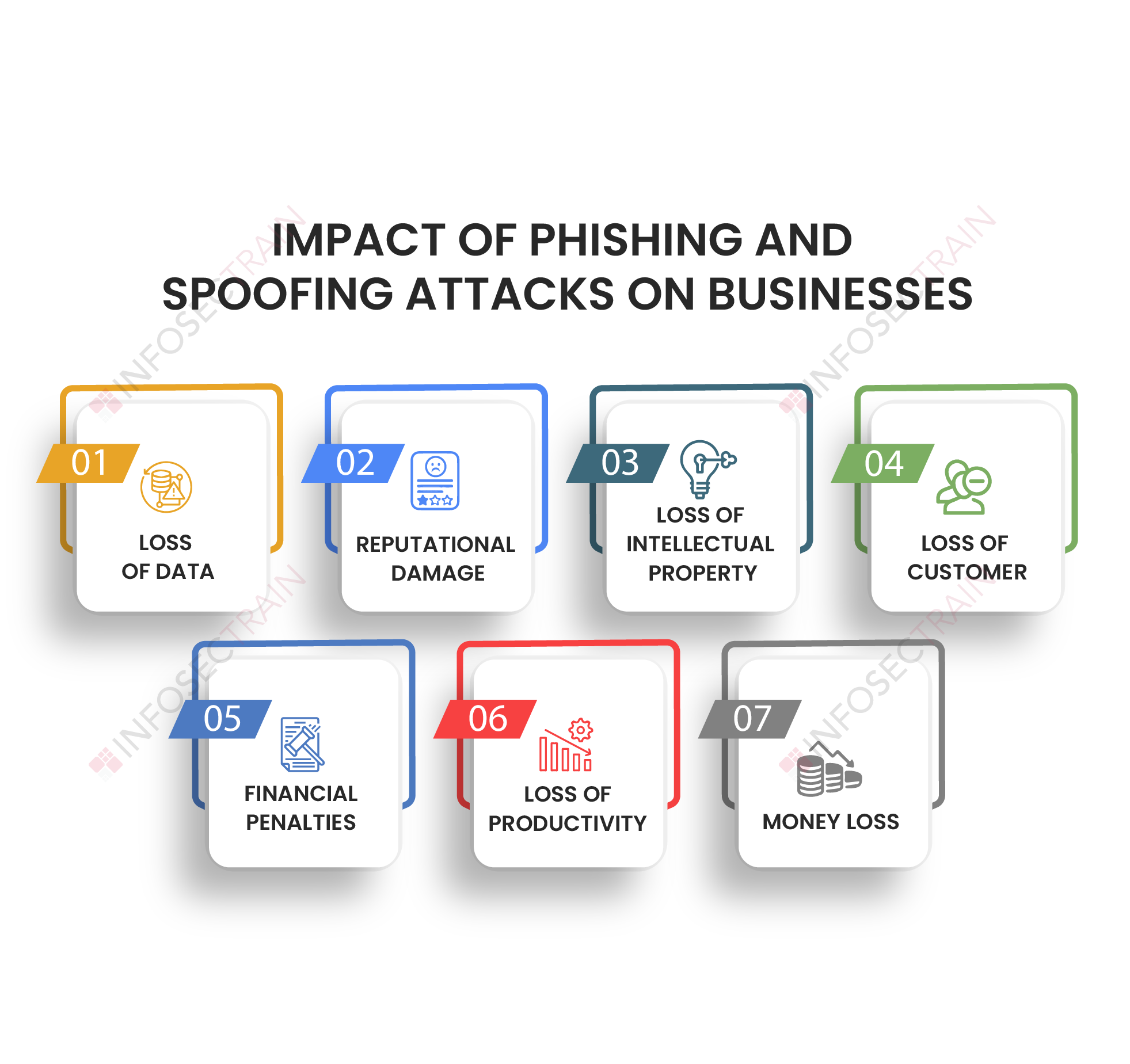
1. Loss of Data
A malicious actor can potentially gain unauthorized access to an organization’s data and systems by exploiting a human vulnerability and manipulating individuals into disclosing sensitive information or clicking on malicious links. When an employee falls victim to such an attack and unknowingly provides access credentials or clicks on a harmful link, a malicious actor can gain unauthorized access to the organization’s data and systems. The most severe consequence of phishing and spoofing attacks is data loss.
2. Reputational Damage
Businesses suffer reputational damage due to a data breach caused by phishing and spoofing attacks. When a breach is revealed, the general public loses trust in the organization. Irrespective of an organization’s previous reputation, the occurrence of data breaches has a detrimental effect on its brand image, often leading to a perception of unreliability among stakeholders for an extended period following a successful breach.
3. Loss of Intellectual Property
The intellectual property holds immense value as a business asset, often surpassing monetary or equipment worth. Phishing and spoofing attacks pose a significant threat, leading to intellectual property theft. Businesses heavily invest in research, development, innovative technologies, and trade secrets. Compromise of such assets can cause setbacks, reducing success and competitiveness in the market.
4. Loss of Customer
As per a UK poll, over 50% of customers refrain from purchasing from an organization that has experienced a data breach for a significant duration. In 41% of instances, customers have discontinued visiting businesses that suffered data theft, and this negative sentiment may persist for an extended period. The poll’s findings underscore the substantial impact of data breaches on consumer trust and behavior, necessitating diligent efforts by organizations to implement robust cybersecurity measures and regain customer confidence in the long term.
5. Financial Penalties
When sensitive consumer information becomes public, the offending company is found responsible. In addition to the immediate monetary loss resulting from a failure to protect against phishing and spoofing, significant regulatory fines for mishandling consumer data can be imposed on an organization.
6. Loss of Productivity
Phishing and spoofing attacks result in data breaches or disrupt company processes. After a successful attack, a significant portion of an organization’s time will be spent attempting to retrieve stolen data and analyzing the breach, leaving little time for actual business. This results in reduced employee productivity as systems are taken offline for reconfiguration and maintenance, diverting resources from core business activities.
7. Money Loss
Money loss due to phishing and spoofing attacks may stem from compensating affected customers or employees whose personal data was stolen. Additionally, cybercriminals can exploit impersonation to transfer funds from a company’s account, necessitating extra expenses for incident management and financial recovery.
A successful phishing or spoofing attack can have a lot of consequences for a business. Data loss, compromised credentials, ransomware, and malware infestation are possibilities. Let’s look at some of the most recent phishing attack reports:
- According to the cybersecurity vendor’s 2022 Q1 Brand Phishing Report, phishing attacks imitating the corporate social networking website accounted for more than half (52%) of all attacks worldwide in the first quarter of 2022. This is a 44% rise over the previous quarter, Q4 2021 when LinkedIn was the seventh most impersonated enterprise.
- According to Proofpoint’s 2022 State of the Phish report, more than 9 out of 10 (91%) UK firms were successfully hacked by an email phishing attack last year.
- According to the Avanan report, enterprising hackers have discovered a technique to create convincing phishing emails that employ Google Docs and Drive features to avoid security filters.
- According to Barracuda Networks, phishing emails have increased by over 600 % since the end of February as cybercriminals seek to benefit from the fear and uncertainty caused by the COVID-19 outbreak.
- According to a new study from the Healthcare Information and Management Systems Society (HIMSS), phishing and spoofing attacks are the most severe security issues affecting all healthcare companies.
You must emphasize staff cybersecurity education, install advanced security solutions, and create rules to prevent phishing attacks and protect your business from any consequences.
How can InfosecTrain help?
Phishing and spoofing attacks can have significant repercussions on businesses, resulting in data breaches, financial losses, and damage to reputation. As a leading training organization, InfosecTrain offers the Certified Ethical Hacker (CEH) certification training course, equipping individuals with the expertise to safeguard businesses from these cyber threats. CEH-trained professionals are adept at simulating attacks, performing security assessments, and providing security awareness training, empowering organizations with proactive defense and incident response capabilities. By enrolling in this course, businesses can strengthen their cybersecurity defenses, protecting their valuable assets, brand reputation, and overall security posture.

TRAINING CALENDAR of Upcoming Batches For CEH v12
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 10-Mar-2024 | 27-Apr-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Apr-2024 | 12-May-2024 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 27-Apr-2024 | 02-Jun-2024 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
