CompTIA CySA+ Domain 2: Software and Systems Security
Information Technology (IT) has revolutionized by leaps and bounds in the last few years. It has opened up new possibilities for businesses and how we go about our daily lives, and the ability to organize the massive amount of data at our fingertips. However, most businesses have well-oiled systems dedicated to developing, releasing, and maintaining viable software and systems. Nonetheless, the rising concerns and risks associated with insecure software have raised awareness of the necessity to incorporate security into the development process. Businesses and organizations have had to up their game with the concern of rising system threats.

Software and systems security is an important aspect to keep software and systems in control and working effectively. The CompTIA CySA+ certification deals with the various aspects related to software and systems security.
The CompTIA Cybersecurity Analyst+ certification (also known as CySA+) is a vendor-neutral certification for cybersecurity, threat, and vulnerability analysts. It focuses on security analytics and the actual application of security solutions in real-world situations.
Domains of CySA+
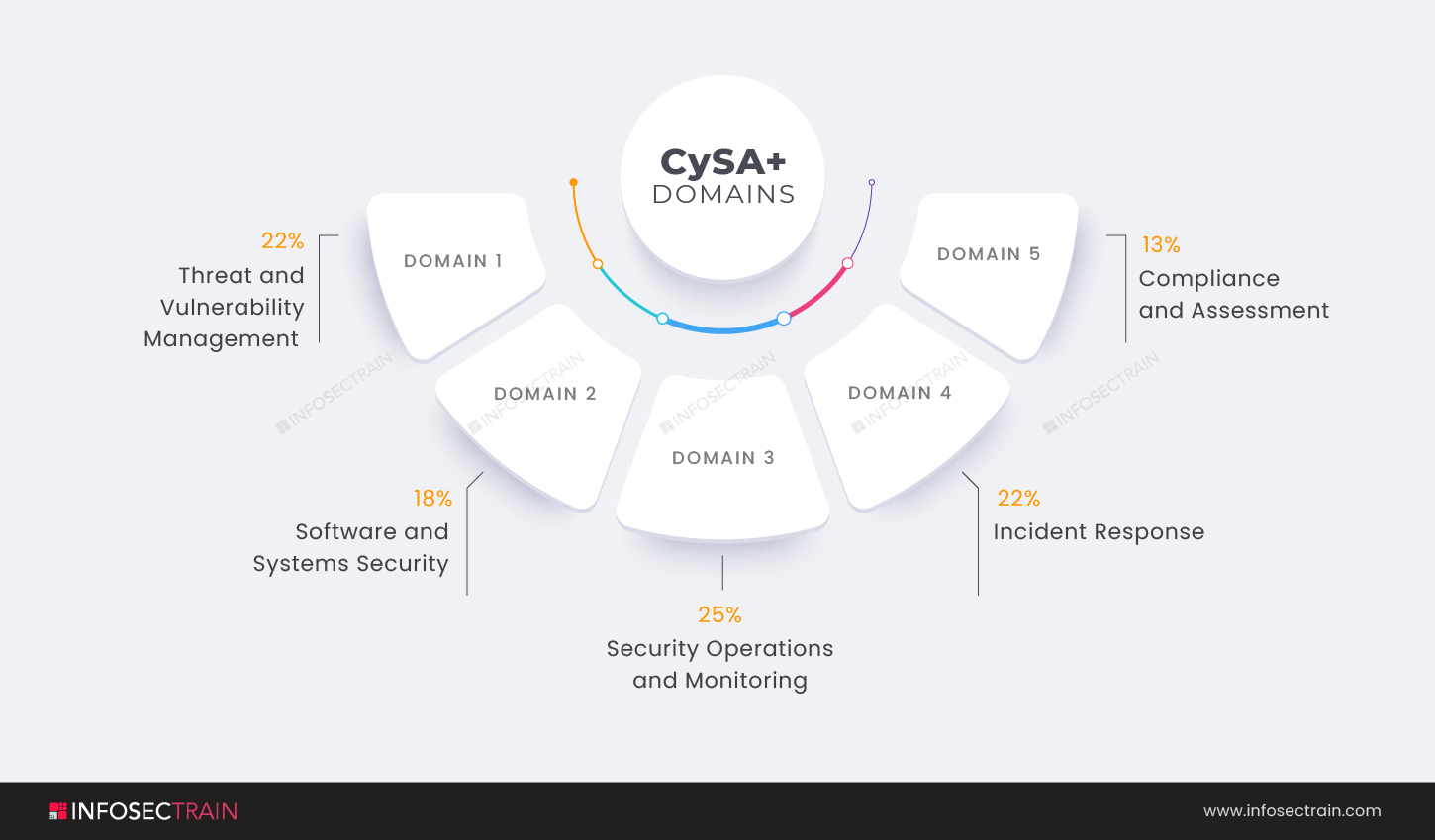
- Domain 1: Threat and Vulnerability Management (22%)
- Domain 2: Software and Systems Security (18%)
- Domain 3: Security Operations and Monitoring (25%)
- Domain 4: Incident Response (22%)
- Domain 5: Compliance and Assessment (13%)
This article provides an overview of the CompTIA CySA+ Domain 2: Software and Systems Security.
CompTIA CySA+ Domain 2: Software and Systems Security
Software and Systems Security is the second domain in the CompTIA CySA+ certification exam. The domain comprises 18% weightage. In the second domain of the CySA+ certification, you will learn how to assess and integrate security into your organization’s software and hardware, as well as how to use the Software Development Life Cycle (SDLC) and its security implications to ensure that the software your organization uses is well-written and secure throughout its lifespan. It will discuss how to ensure that any cloud services you might inject into your environment are secure to support your apps and systems and best practices to develop a secure environment. Security is vital to provide integrity, authentication, and availability.
Software security is a type of computer security that focuses on the secure design and implementation of software using the most up-to-date technologies, tools, and methods. In other words, it focuses on avoiding software flaws, bugs, and vulnerabilities. Security is essential for a device to function at its best, from authentication to software updates, anti-virus protection, and customizations. On the other hand, all aspects of accessing information assets are covered by system security.
The second domain of the CompTIA CySA+ certification exam covers the following subtopics:
- Given a scenario, apply security solutions for infrastructure management
- Explain software assurance best practices
- Explain hardware assurance best practices
1. Given a scenario, apply security solutions for infrastructure management: This subsection will discuss the security solutions for infrastructure management. It covers the critical areas associated with Identity and Access Management (IAM) to reflect a broader identity in a world of numerous connected devices, people, and processes. The section will discuss the two main infrastructure models: cloud vs. on-premises. The domain will also cover the issues surrounding asset management, including asset tagging and change management. It will teach you how to describe physical and virtual segmentation, jump boxes, and system isolation with an air gap. The section will also cover the physical, software-defined, Virtual Private Cloud (VPC), Virtual Private Network (VPN), and serverless architectures.
2. Explain software assurance best practices: Software assurance refers to the development and execution of methods and processes for verifying that software performs as intended while limiting the risks of vulnerabilities, malicious code, or faults that could affect the end-user. This subsection examines application security, the types of testing to perform, and secure coding best practices from a number of well-known organizations that issue security guidelines. It is preferable for software to be secured from the start. The earlier security is incorporated in the software development process, the less it will cost to secure the software.
This section discusses the platforms such as web application, mobile, client/server, embedded, and System-on-Chip (SoC), Software Development Life Cycle (SDLC) integration, discusses the DevSecOps framework, various software assessment methods, best practices for secure coding, static and dynamic analysis tools, more structured techniques of analysis for verification of critical software, and service-oriented architecture.
3. Explain hardware assurance best practices: This subsection covers critical hardware security subjects such as dedicated hardware, hardware encryption, secure processing, trusted foundries, and anti-tamper measures. Hardware root of trust, eFuse, the Unified Extensible Firmware Interface (UEFI), trusted foundry, Self-Encrypting Drives (SED) will all be covered. You will learn about secure boot processes and secure processing as well.
CompTIA CySA+ with InfosecTrain
InfosecTrain, a significant provider of Information Technology and cybersecurity training, offers the CompTIA CySA+ certification training course. We assist participants in our training program by teaching system security principles, with a focus on the security aspects and implications of software and information technologies. Every step of the journey, our trainers will be there for you! So get started with InfosecTrain today to prepare for the CompTIA Cybersecurity Analyst (CySA+) certification exam. We are also CompTIA’s authorized training partner.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
