CompTIA CySA+ Domain 4: Incident Response
What happens when an attack is carried out within an organization? They usually do not know they have been targeted; therefore, they do not do anything. However, once they discover it, the most common reaction is panic, as it is similar to being mugged.
When an organization’s reputation, income, and customer trust are at stake, the ability to detect and respond to cybersecurity incidents and events is vital. The earlier your company can identify and respond to a data breach or even a security event, the less likely it is to significantly impact your data, customer trust, reputation, and revenue. A structured strategy to dealing with and managing the consequences of a security breach or cyberattack is incident response.
What use would it be to be a Cybersecurity Analyst if you didn’t know how to respond to a security incident? The CompTIA CySA+ certification prepares IT professionals to detect and respond to any security incident or event that may occur. The goal is to provide knowledge to manage the situation in such a way that harm is limited and recovery time and expenditures are minimized.
Domains of CySA+
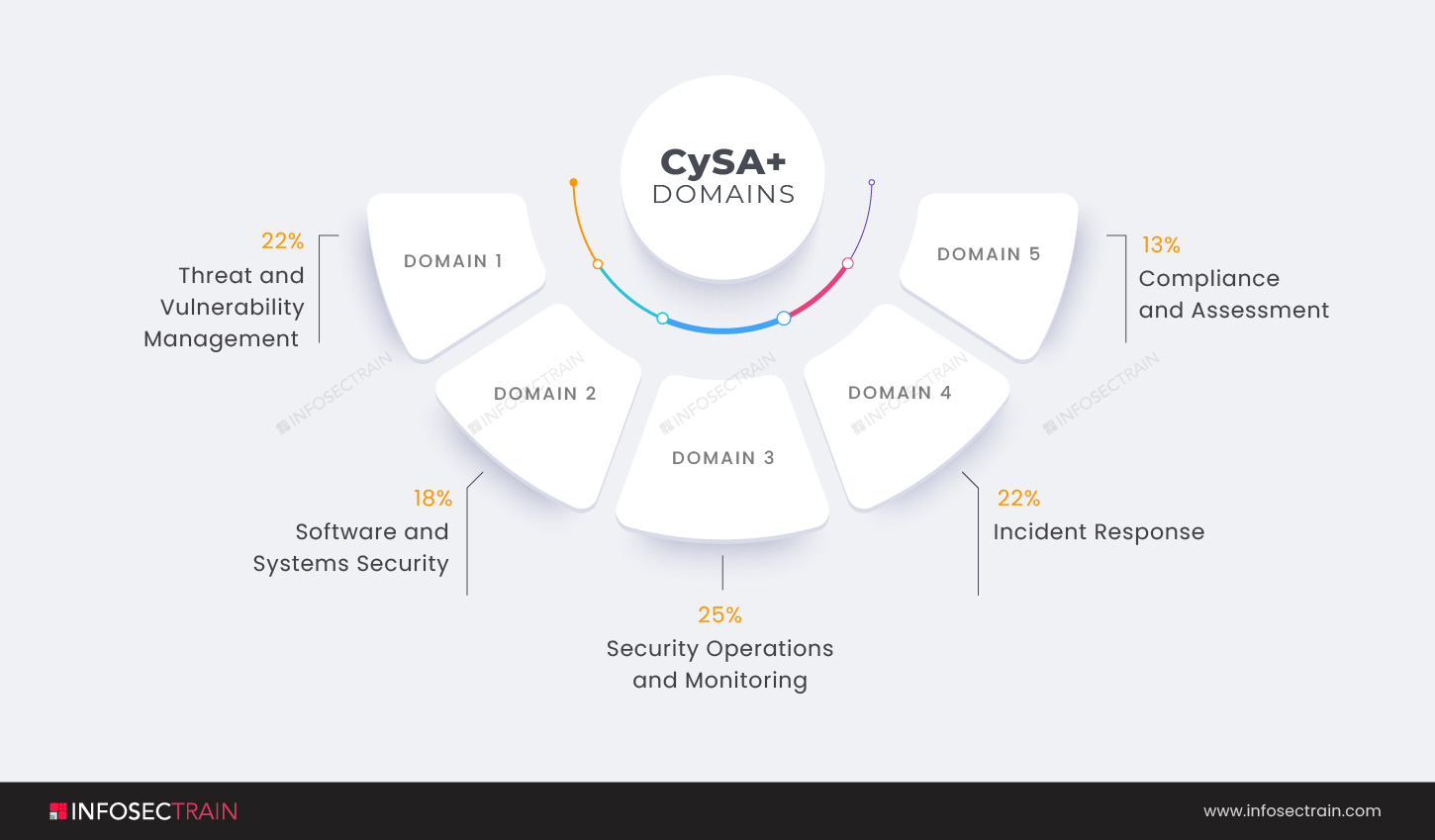
- Domain 1: Threat and Vulnerability Management (22%)
- Domain 2: Software and Systems Security (18%)
- Domain 3: Security Operations and Monitoring (25%)
- Domain 4: Incident Response (22%)
- Domain 5: Compliance and Assessment (13%)
This article gives an overview of the CompTIA CySA+ Domain 4: Incident Response.
CompTIA CySA+ Domain 4: Incident Response
The fourth domain of the CompTIA Cybersecurity Analyst (CySA+) certification exam is Incident Response. The domain comprises 22% weightage. When you have completed this domain, you will have the skills, knowledge, and preparation to deal with a security incident or event. You will learn how to classify threats and analyze the impact of cybersecurity incidents, the significance of communication throughout a cybersecurity incident response effort, the symptoms of an ongoing incident, how to use forensic tools, and how to recover from an incident.
The fourth domain of the CompTIA CySA+ certification exam covers the following subtopics:
- Explain importance of the incident response process
- Given the scenario, apply the appropriate incident response procedure
- Given an incident, analyze potential indicators of compromise
- Given the scenario, utilize basic digital forensics techniques
1. Explain importance of the incident response process
Responding immediately to an incident will help an organization minimize damages, mitigate exploited vulnerabilities, restore services and procedures, and lower the risk of future incidents. The primary purpose of incident response is to limit the scope of an incident, minimize the threat to organizational systems and data, and promptly restore impacted systems and data to operational status.
This section will explore the importance of the incident response process within an organization and explain the significance of communication during the incident response process. This section includes the communication plan like limiting communication to trusted parties, using a secure method of communication, preventing accidental release of information, reporting requirements, response coordination with relevant entities like legal, human resource, regulatory bodies, and more. The section also covers various factors contributing to data criticality.
2. Given the scenario, apply the appropriate incident response procedure
This section deals with the application of an effective incident response procedure. Every incident response strategy should include several steps, which include preparation, detection and analysis, containment, eradication and recovery, and post-incident operations, to successfully cover all bases and address the wide spectrum of potential security threats. A robust incident response plan should enable you to deal with a wide range of events that could potentially harm your business. Each possible scenario should be described in the plan and the procedures taken to reduce the damage.
3. Given the incident, analyze potential indicators of compromise
The section delves into the most common network, host, and application symptoms that could indicate a compromise. Data that suggest a cyber attack has infiltrated a system are Indicators of Compromise (IOCs). They provide critical information to cybersecurity professionals in the aftermath of a data breach or other security breach. You will learn how to evaluate these potential Indicators of Compromise (IOCs).
4. Given the scenario, utilize basic digital forensics techniques
This section will discuss the basic digital forensics techniques. It describes how to distinguish threat data or behavior in order to determine the severity of an incident, put together a toolkit, and use relevant forensics tools during an investigation. It includes network, endpoint, memory, mobile, cloud, virtualization, legal hold, procedures, hashing, carving, and data acquisition.
CompTIA CySA+ with InfosecTrain
InfosecTrain, a significant provider of IT and cybersecurity training and an authorized partner of CompTIA, offers the CompTIA CySA+ certification training course. We assist participants in understanding how to respond to cyber incidents in order to ensure that the Cybersecurity Analyst is prepared for a variety of security incidents, such as a breach or cyberattack, as well as develop a response plan to provide an organized approach to deal with a cyber incident and manage the aftermath. Thus assist them in preparing for the incident response domain. Our instructors will support you throughout your certification process. So you may enroll in the CompTIA CySA+ certification training course with InfosecTrain right now.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
