CompTIA PenTest+ Domain 4: Reporting and Communication

Domains of CompTIA PenTest+:
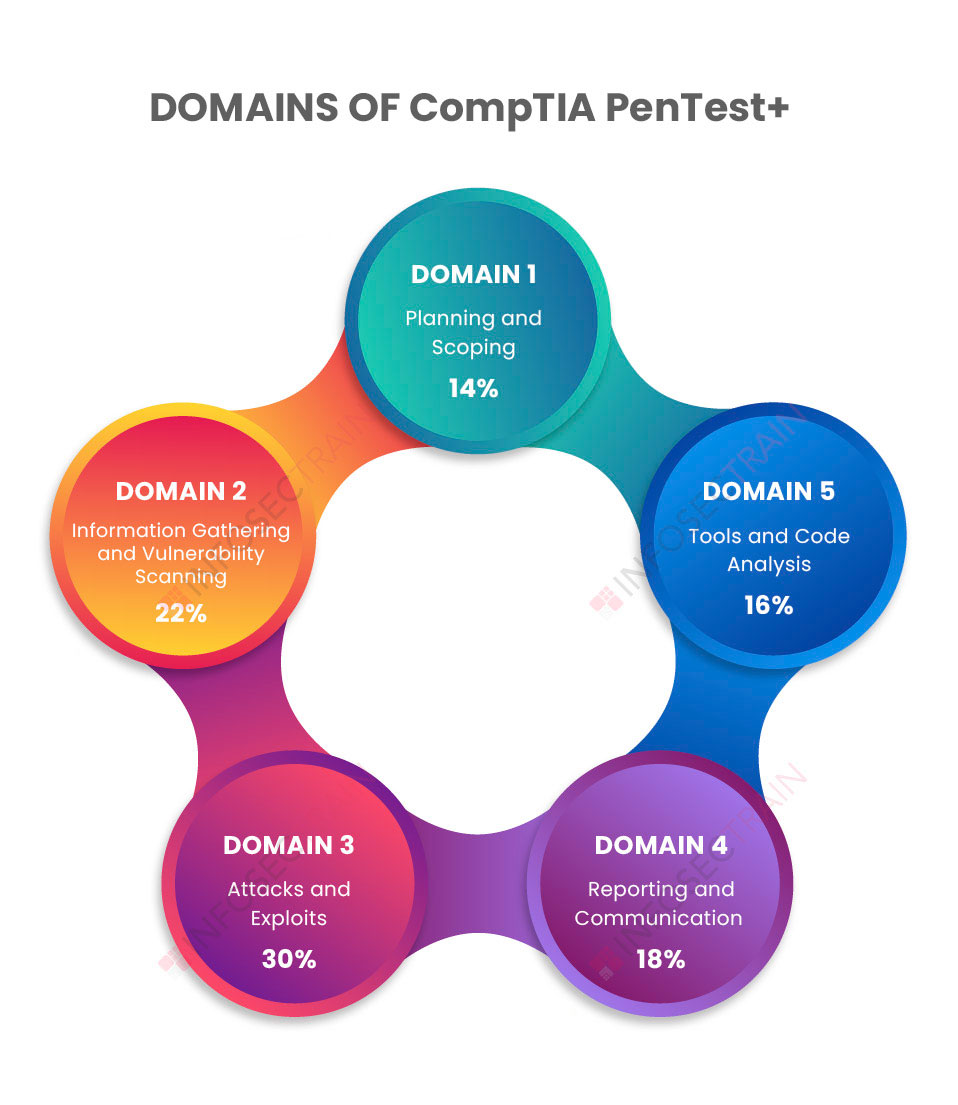
- Domain 1: Planning and Scoping (14%)
- Domain 2: Information Gathering and Vulnerability Scanning (22%)
- Domain 3: Attacks and Exploits (30%)
- Domain 4: Reporting and Communication (18%)
- Domain 5: Tools and Code Analysis (16%)
This article explores domain 4 of CompTIA PenTest+ certification, which is Reporting and Communication.
CompTIA PenTest+ Domain 4: Reporting and Communication
“Reporting and Communication” is one of the most important parts of the penetration testing process. This CompTIA PenTest+ certification exam domain covers a weightage of 18%. Penetration testing will be ineffective without effective reports and communication. What good are penetration tests if the organization can not decipher the results and work to address the flaws to improve its security posture? Nothing, right? As a result, reporting and communication become crucial components of the penetration testing process in order to assess the organization’s current security posture and the activities required to improve it. The domain focuses on producing a complete analysis of the vulnerabilities discovered during the penetration test, as well as remediation actions. The report should include a complete list of vulnerabilities, as well as a POC (Proof of Concept) and remediation recommendations to address those issues first. It also assigns a score to each discovered security issue based on how much it may affect an organization’s systems, applications, or software. The need for efficient communication is also emphasized in this domain. Communication is crucial not only after a successful penetration test but throughout the entire process, beginning with the decision to conduct the test.
This domain is further divided into four subsections:
- Compare and contrast important components of written reports
- Given a scenario, analyze the findings and recommend the appropriate remediation within a report
- Explain the importance of communication during a penetration testing process
- Explain post-report delivery activities
1. Compare and contrast important components of written reports
A structured written report is an important deliverable after a penetration test. It is essential to provide details on what Penetration Testers have identified, convey how they approached the penetration test, communicate blockers, offer remediation plans, and share all relevant information about the security test. The section discusses the key concepts for reporting, such as appropriately tailoring content to their audiences, which includes developers, technical staff, security teams, C-suite, and third-party stakeholders.
A Penetration Tester compiles the results of penetration tests conducted into a report that details particular vulnerabilities that were exploited, methodologies used, sensitive data that was accessed, the period the Penetration Testers were able to remain undetected in the target system, and the conclusion of the test.
The domain then examines the test report storage time and the safe delivery of the reports to the audiences. The various approaches for documenting reports, as well as the core causes of the findings, are also discussed.
2. Given a scenario, analyze the findings and recommend the appropriate remediation within a report
The Penetration Tester needs to provide remediation to the security gaps and vulnerabilities discovered during the penetration test to help organizations improve their security posture. The report should offer appropriate solutions to the security issues found to gain full advantage of the assessment. This section of the domain focuses on the Penetration Tester’s ability to analyze the test findings and create an appropriate remediation strategy for the discovered findings, such as vulnerabilities, security gaps, etc. These recommendations include security controls that fall into technical, administrative, operational, and physical controls.
Technical controls for remediating security flaws include system hardening, encrypting the passwords, sanitizing the user input, certificate management, patch management, network segmentation, implementation of multifactor authentication, and more.
Administrative controls for remediating security flaws include role-based access control, secure software development life cycle, minimum password requirements, policies, and procedures.
Security issues arise not only as a result of technical defects in the system but also as a result of the role of people inside the company. Therefore, operational controls are critical for an organization’s security. Job rotation, time-of-day limitations, user training, and mandated vacations for staff are operational measures for resolving security problems.
Furthermore, the section covers physical controls such as access control vestibule, biometric controls, and video surveillance to improve the organization’s security posture.
3. Explain the importance of communication during a penetration testing process
The success of the penetration testing process is dependent on effective communication. It is critical since it aids both the penetration test team and the client in establishing a positive working relationship and achieving their objectives. As a result, Penetration Testers communicate with their clients throughout the penetration testing process. It is also crucial to explain clearly in the penetration testing report so that the customer can put any recommendations into action and improve their organization’s security posture.
Therefore this section is all about establishing effective communication between the Penetration Testers and members of the organizations involved in the process. The section discusses how to set up the communication path with the primary, technical, and emergency contacts within their target organization.
The section covers the triggers for communication, like critical findings, status reports, indicators of prior compromise, and the reasons for communication.
The section also delves into the conditions when reprioritization of penetration test objectives is necessary and how the concerned persons can effectively communicate. In addition, the section also covers how to effectively communicate the findings in a report to different audiences.
4. Explain post-report delivery activities
The penetration testing process does not end when the assessment is completed, the report is delivered, or when effective communication is achieved. Penetration test teams must also clean up after the security test in the target organization and reflect on the process. During the assessment, the Penetration Testers or penetration testing teams create or install backdoors, test accounts, malware, codes, tools, and more in the target organization’s systems, which must be cleared after the penetration testing engagement. As a result, this section describes the cleanup actions after a penetration testing engagement, such as removing shells, credentials, and tools.
The customer must accept the results in writing and complete the assessment process, which will be covered. Penetration Testers are required to follow up on the processes and, if necessary, retest the results. The section also discusses ways to verify the accuracy of the findings.
The section also teaches how to reflect on the findings and extract lessons to keep evolving, and also, after the engagement, how to erase the customer’s sensitive data.
CompTIA PenTest+ with InfosecTrain
Penetration testing techniques necessitate excellent communication and reporting of findings and solutions to improve the organization’s security posture. The CompTIA PenTest+ certification enables you to report and explain the results of your tests. Enroll in InfosecTrain’s CompTIA PenTest+ certification training and learn from our experienced instructors to improve your reporting and communication abilities. We are a renowned IT security training provider.



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
