CCSP Domain 6: Legal, Risk, and Compliance
With the advent and expansion of cloud computing, the risks and threats in the cloud environments have also soared. It has increased the demands for professionals who are skilled to secure these cloud environments. To meet this enlarged demand for qualified professionals, the (ISC)2 and Cloud Security Alliance (CSA) collaborated in 2015 to create the Certified Cloud Security Professional certification, abbreviated as CCSP.

The CCSP credential is designed to ensure that the professionals have the knowledge and skills needed to design, implement, operate, control, and enforce secure cloud environments across diverse industries.
The CCSP CBK covers a broad spectrum of topics related to security in cloud environments. The certification verifies your knowledge and skills in six domains. They are:
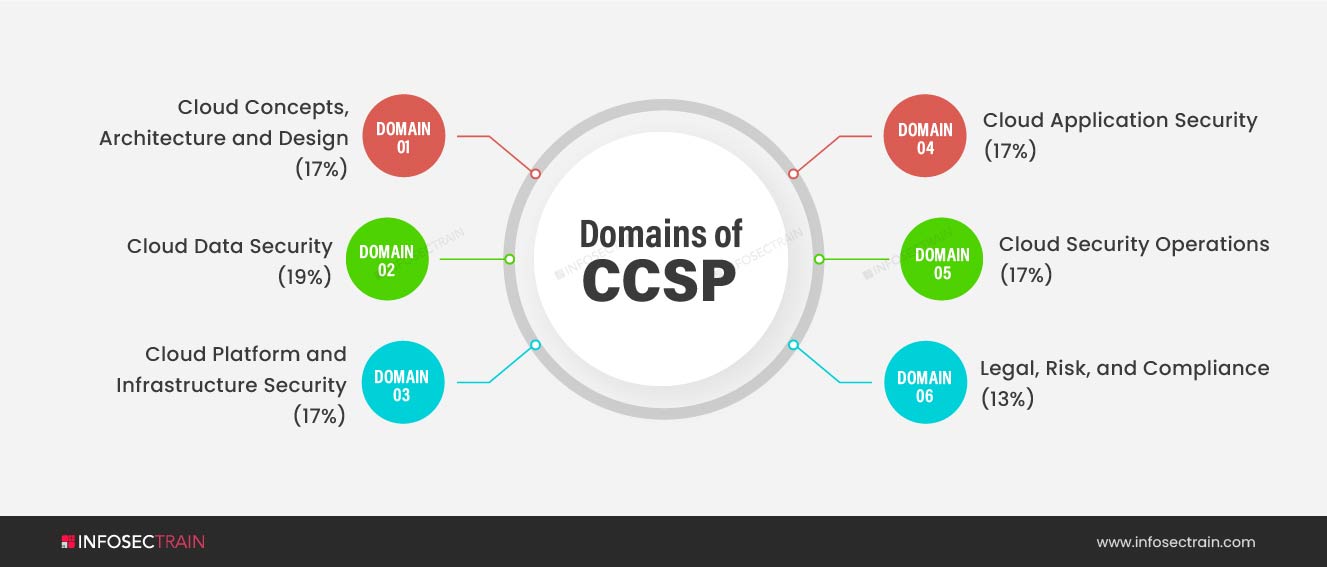
- Domain 1: Cloud Concepts, Architecture and Design (17%)
- Domain 2: Cloud Data Security (19%)
- Domain 3: Cloud Platform and Infrastructure Security (17%)
- Domain 4: Cloud Application Security (17%)
- Domain 5: Cloud Security Operations (17%)
- Domain 6: Legal, Risk, and Compliance (13%)
This article will go over the sixth domain of the CCSP certification and what a candidate can expect in the exam.
Legal, Risk, and Compliance
Domain 6 is concerned with the legal and regulatory requirements for IT systems, as well as how they apply to cloud computing and its numerous dimensions. It holds the weightage of 13% in the CCSP certification exam and covers the following topics:
- Articulate Legal Requirements and Unique Risks within the Cloud Environment
- Understand Privacy Issues
- Understand Audit Process, Methodologies, and Required Adaptations for a Cloud Environment
- Understand Implications of Cloud to Enterprise Risk Management
- Understand Outsourcing and Cloud Contract Design
You can also view the video given below to learn more about the CCSP Domain 6 exam outline in detail.
Below is the overview of various sections of the sixth domain of CCSP and what candidates can expect in the exam from this domain.
Articulate Legal Requirements and Unique Risks within the Cloud Environment
Because cloud computing frequently spans several national and geographical borders, it poses various new risks and concerns. As a result, it is subjected to a variety of requirements, some of which are in direct contradiction with one another.
This domain examines legal controls mandated by many nations and legal risks unique to cloud computing. The contrasts between contractual and regulated personal data safeguards and the precise definitions and legal requirements for personal information and privacy as they pertain to jurisdictional restrictions are discussed.
Understand Privacy Issues
eDiscovery orders and the necessity to furnish documents or data in response to a formal court order or request are two of the most common legal consequences on any IT system or application. The topic delves into the entire notion of eDiscovery and digital forensics, particularly as they pertain to cloud computing and the unique issues that come with it. Because the cloud customer will not have the type of access required to perform data collection, many of the tools and processes that people are familiar with for both areas will not be directly feasible in a cloud environment. Such requests must be addressed through contracts and other formal processes.
Understand Audit Process, Methodologies, and Required Adaptations for a Cloud Environment
The auditing process is one of the most crucial components of IT security and compliance. Domain 6 explores the several types of audits, their aims, and legal obligations, as well as their implications on cloud computing. One of the most challenging characteristics of cloud computing is gaining visibility and access to the underlying infrastructure on behalf of the cloud customer.
Another one is how cloud providers use audits and auditing reports to ensure confidence in security programs for multiple customers without giving each customer access or perform numerous infrastructure audits. Domain 6 delves further into the auditing and certification standards, the most often used auditing paradigms and reports, the appropriate application and audience for each, and the right identification of essential stakeholders.
Understand Implications of Cloud to Enterprise Risk Management
Domain 6 also delves into risk management, as well as its specific applications and issues about cloud computing. The emergence of cloud computing and the loss of direct control can become critical aspects of risk management inside a company, requiring careful consideration and analysis. Risk management methods and procedures, as well as risk frameworks and assessment methodologies, are all covered.
The four stages of this risk assessment method are framing, assessing, responding, and monitoring. Each stage builds on the previous one, begins with the definition of the process and risk categories, conducts the assessment, determines appropriate responses or accepts any identified risks, and then monitors those risks for future evolution or changes in response strategies. Risk can be accepted, avoided, transferred, or mitigated in general, or a combination of these strategies can be employed.
Understand Outsourcing and Cloud Contract Design
Finally, Domain 6 addresses the various concerns and requirements related to contract management and scoping for cloud hosting engagements. This includes advice on how to choose a cloud provider, the key elements and issues that must be addressed in the contract that are unique to cloud hosting, and the concerns that a cloud customer will have.
CCSP with InfosecTrain
If you desire to advance your IT career in cloud security, the CCSP certification is the right choice for you. The CCSP is the most acclaimed yet one of the challenging credentials for cloud security professionals to obtain. But to take guidance from a professional is the best approach to follow when you prepare for the CCSP certification exam or any challenging certification exam, for that matter. So, you can enroll in the CCSP certification training course at InfosecTrain. We are a well-known IT security certification and training provider. Our course will provide you with a concrete foundation to take and pass the CCSP certification exam with the proper assistance of our qualified instructors.
To be acquainted with the CCSP certification, you can also watch the following video:



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
