How does Microsoft Sentinel work?

Table of Contents
What is Microsoft Sentinel?
Stages of Microsoft Sentinel
How does Microsoft Sentinel work?
What is the relation between Microsoft Sentinel and Microsoft Defender for Cloud, and how do they work together?
What is Microsoft Sentinel?
In Microsoft’s public cloud platform, Microsoft Sentinel is a Security Information and Event Management (SIEM) and Security Orchestration and Automated Response (SOAR) system that combines attack detection, threat visibility, proactive hunting, and threat response into a unified platform.
Microsoft Sentinel is a single solution that can handle both SIEM and SOAR. A SIEM solution collects data and analyses security warnings in real-time. SOAR is a set of software solutions and tools that help businesses streamline their security operations.
You can refer to the following to know more about Microsoft Sentinel:
Stages of Microsoft Sentinel
Microsoft Sentinel is divided into four stages:
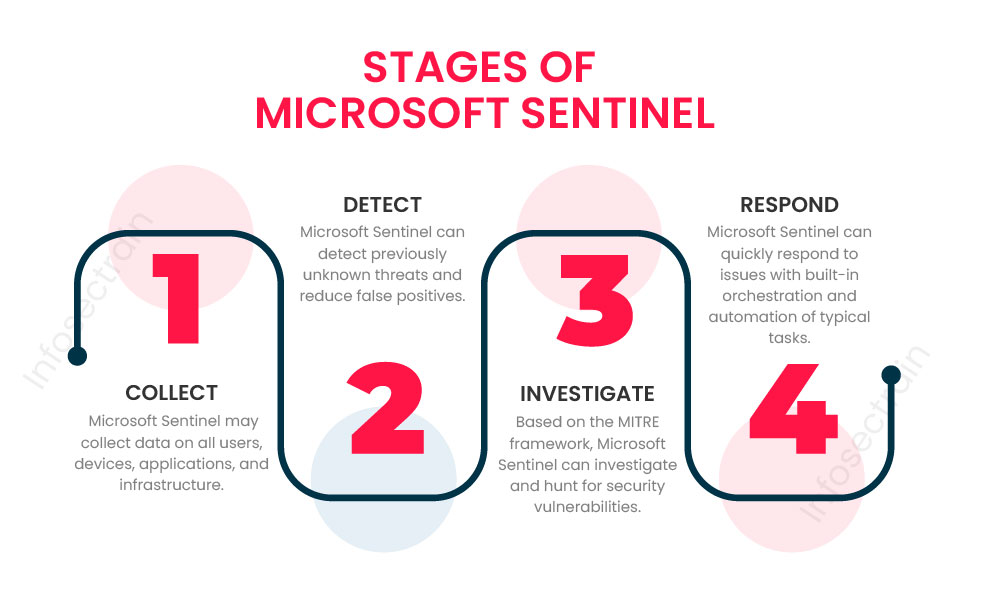
- Collect: Microsoft Sentinel may collect data on all users, devices, applications, and infrastructure, whether on-premises or across different cloud environments. It has an easy-to-use interface for connecting to security sources right out of the box. For Microsoft products, there are various connectors that offer real-time integration.
- Detect: Microsoft Sentinel can detect previously unknown threats and reduce false positives using Microsoft’s unrivaled threat intelligence and analytics. Azure Analytics serves a crucial role in matching alerts with security team-identified issues. It comes with built-in templates for creating threat detection rules and automating threat responses right out of the box. Aside from that, Microsoft Sentinel also allows for the creation of custom rules.
- Investigate: Based on the MITRE framework, Microsoft Sentinel can investigate and hunt for security vulnerabilities. It can use Artificial Intelligence to proactively discover risks across the protected assets before an alarm is triggered. The information linked with and created by Microsoft Sentinel is freely accessible in the form of tables that may be queried.
- Respond: Microsoft Sentinel can quickly respond to issues with built-in orchestration and automation of typical tasks. It can use playbooks to create a more straightforward security orchestration. When an event occurs, it can also create tickets in ServiceNow, Jira, and other systems.
How does Microsoft Sentinel work?
Data Connectors are first used to feed data from devices and services into Microsoft Sentinel. Then the data is sent to Azure Log Analytics. Workbooks are used to visualize data, potential problems, and trends and aid in the development of specific queries. These queries could help you create analytics rules. After you have set up analytic rules, you will be able to see incidents and take automated actions with Playbooks. When investigating incidents, you can leave a trail of Bookmarks to flag interesting or anomalous data for further investigation and identify additional locations that may be affected. Finally, you may go threat hunting.
Because Microsoft provides built-in queries and analytics, you are unlikely to need to create your own right away. You can also create custom workbooks to see your data in the way you choose.
All Microsoft Sentinel-related data is stored in Microsoft Sentinel. It features high-performance querying, a dynamic schema, and the ability to expand to huge data volumes. This data can also be analyzed using external tools like Jupyter notebooks and Python.
All data fed into Microsoft Sentinel must originate on a Log Analytics workspace. Analytics – Custom rule sets that can search all imported data for threats. Playbooks are a type of automated response to warnings triggered by Analytics. Hunting — Enables proactive, manual inquiries into potential security issues.
What is the relation between Microsoft Sentinel and Microsoft Defender for Cloud, and how do they work together?
Microsoft Sentinel is a cloud-native SIEM that collects logs from various data sources and determines what kind of malicious activity has occurred from those events, analyses that data, and allows you to investigate and take action on it. These data sources that Sentinel collects can be internal, and one of those data sources is Microsoft Defender for Cloud.
It can be third-party or even custom, and it would be anywhere where we do not have a built-in connector already enabled, but in the case of Microsoft Defender for Cloud, what’s really flowing into Sentinel or the alerts that come from Microsoft Defender for Cloud detections, and that would be on IaaS and PaaS resources.
So Microsoft Defender for Cloud sends its alerts and logs information into Sentinel that can be correlated with other contextual information security centers. It does more than allow the investigation of alerts from the security center. You have two main areas.
- Cloud workload protection platform: These are the areas where you aim to minimize the attack surface and ensure that your resources are not vulnerable when they are exposed. Part of it is obtaining detections from it, which means alerts will come from Microsoft Defender for Cloud and pass into central.
- Cloud security posture management: This is where we get recommendations on what it means to be secure, what kinds of vulnerabilities are present, and which Microsoft Defender for Cloud resources are being watched.
Microsoft Sentinel’s native function alerts. Sentinels could broaden this to see more alarms connected to the recognized virtual machine. This could be due to just-in-time VM access, a lack of disc encryption, or misconfigurations that need to be fixed.
Microsoft Sentinel with InfosecTrain
If you desire to learn how Microsoft Sentinel works and how to use it effectively, you can consider enrolling in InfosecTrain’s Microsoft Sentinel training course. You will be able to master the Microsoft Sentinel service after completing this course. This course will also discuss how to integrate Microsoft Sentinel with Microsoft 365.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
