Security Products and Features of AWS
Organizations may increase agility, scalability, innovation, and cost savings by moving production workloads to AWS while retaining a secure environment since AWS provides a variety of tools and capabilities to assist you in achieving your security goals. These tools are similar to the controls you use in your on-premises environments. AWS offers security-specific tools and functionalities across network security, configuration management, access control, and data security. AWS also provides monitoring and logging tools that offer you complete visibility into what’s going on in your environment.
What is AWS Security?
Amazon Web Service (AWS) Security is a set of attributes, tools, or features that make AWS a secure public cloud service provider. AWS is the most adaptable and secure cloud computing platform currently available. You can improve your capacity to meet fundamental security and compliance standards by using Amazon Web Services. AWS is the only commercial cloud that has been evaluated and accepted as secure enough for leading workloads, which benefits all customers.
How does AWS security work?
AWS and its customers follow a concept of shared security responsibility. Customers are in charge of the security of the workloads they deploy on AWS’s infrastructure. You must still follow proper security procedures to safeguard your data and apps, such as monitoring your users. Limit access to sensitive data, for example, or set loose constraints on data designed for public use.
Security in the AWS cloud environment can be divided into two categories:
- Security of the cloud: AWS is responsible for ensuring that its physical cloud infrastructure is secure against potential vulnerabilities and cyber attacks for companies using any AWS services.
- Security in the cloud: It includes cloud-deployed apps or assets, and it is the user’s or company’s responsibility to ensure that their deployed applications or assets on AWS infrastructure are secure against vulnerabilities or cyberattacks.
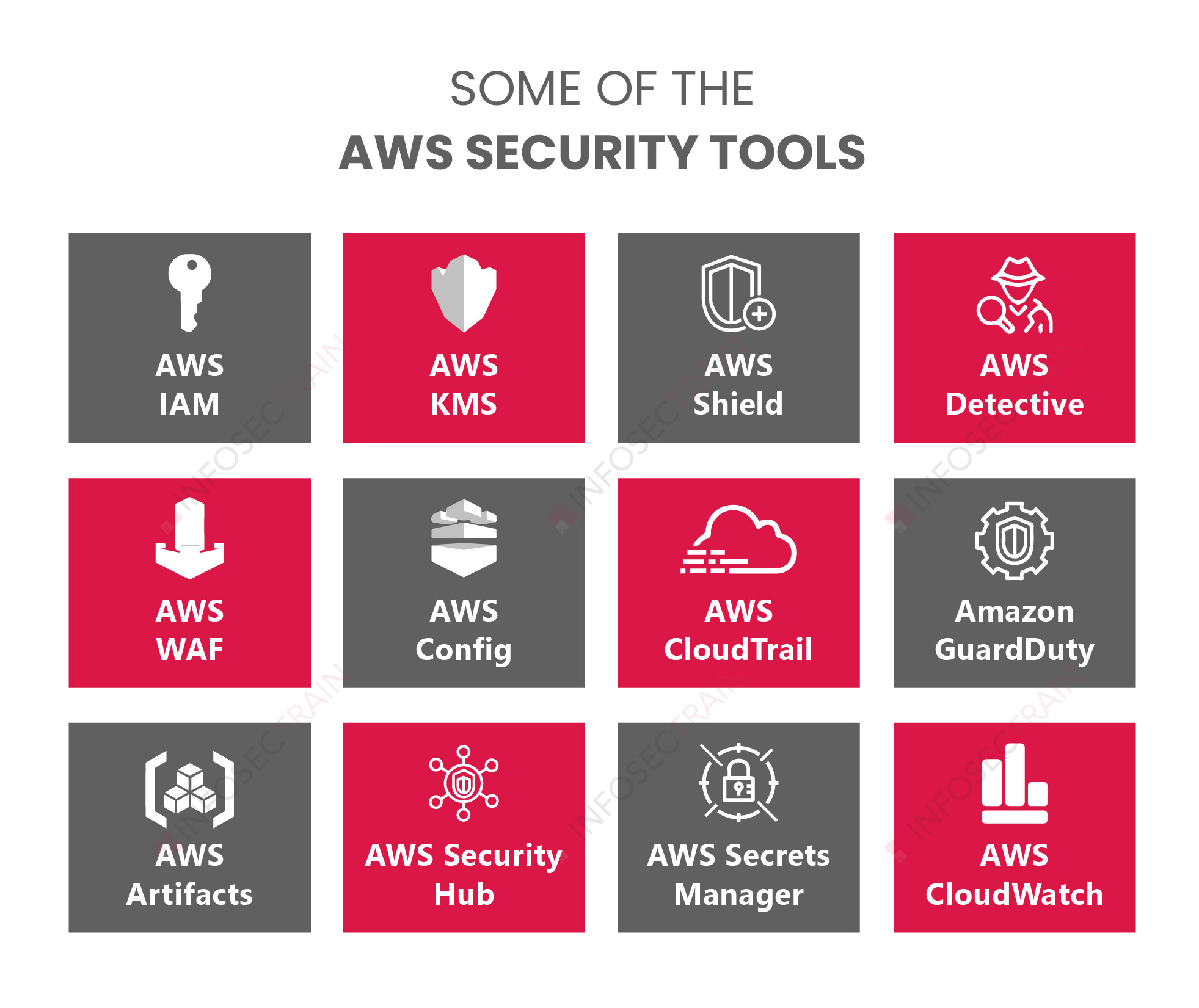
AWS security products and features:
Below is a description of the essential AWS security products and features to keep your cloud safe.
- Security of AWS infrastructure: AWS offers a variety of security features and services to help you protect your data and manage network access. Network firewalls included in Amazon VPC, for example, allow you to construct private networks and manage access to your instances or apps. TLS allows customers to control encryption in transit across all AWS services. Private or dedicated connections from your workplace or on-premises environment are available as connectivity choices. Layer 3 or 4 DDoS mitigation technologies, as well as layer 7 DDoS mitigation technologies, can be included in app and content distribution strategies. All AWS global and regional network traffic between AWS secured facilities are automatically encrypted.
- Identity and Access Management (IAM): Identity plays a very important role in AWS or any other cloud platform. IAM is a free AWS feature that allows you to control who has access to which services and resources. Permissions are extremely fine-grained, allowing you to designate which resources a user has access to. Here are some recommendations for handling your IAM data. After a person checks in, MFA means that they must enter a second code supplied to them via a secondary device, such as a smartphone. Even if a user’s password is compromised, their account will not be accessible with MFA enabled.
- Data Security: A firm grasp of basic data security patterns and precisely mapping these patterns to AWS cloud security policies are required to secure sensitive data in the AWS cloud effectively. You may then apply these controls to implementation-level elements particular to data stores like Amazon Relational Database Service (Amazon RDS) and Amazon DynamoDB, giving you the power and trust you need to run your business securely.
You may use AWS to automate manual security processes to focus on growing and innovating your company. Many AWS client workflows necessitate the ingestion of sensitive and regulated data, such as PCI data, Personally Identifiable Information (PII), and Protected Health Information (PHI). The field-level encryption capability supplied by Amazon CloudFront is one existing approach for sensitive data protection in AWS. At the AWS network edge, this CloudFront capability safeguards critical data fields in requests. Customers can use AWS tools to see what’s going on inside the AWS environment. - Cloud Security Governance: Cloud security governance is a management approach that enables effective and efficient security management and operations in the cloud environment, allowing an organization to meet its business goals. It covers how to use the AWS cloud platform to enforce policies. The decisions you make in terms of technology and governance are the first step in establishing a strong security culture. Security is everyone’s responsibility, so ensure your platform, automation, and metrics help make it easier. AWS computing infrastructures are regularly reviewed, with accreditation bodies granting certifications in a variety of countries and verticals.
- Application Security in Cloud Platform: It includes a set of policies, procedures, and controls that let businesses safeguard applications you deploy and data in AWS cloud environments. In order to protect the business value of your applications, you must first discover any vulnerabilities established throughout the software development process. The AWS Marketplace solutions assist you in identifying, prioritizing, and resolving application vulnerabilities and risks linked with open source or third-party code. Make use of techniques such as MFA. The AWS Network and Application Protection services then offer equally customizable solutions for inspecting and filtering traffic to prevent unwanted access to resources. It protects you at the host, network, and application levels with fine-grained security.
Some of the AWS security tools:
How can InfosecTrain help you with AWS security?
InfosecTrain is a leading IT security training and consulting service provider across the globe specializing in cloud security. You can enroll in our numerous AWS security training courses like AWS Certified Security–Specialty and AWS Cloud Penetration Testing courses based on your needs to gain more information or guidance on AWS security and choose the best AWS security solution for you or your organization.



 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
