Using the Metasploit Framework for Penetration Testing
Penetration testing is an important aspect of an organization’s security strategy as it helps to identify vulnerabilities in their systems and networks before attackers can exploit them. The Metasploit Framework is a popular tool for performing penetration testing as it provides security professionals and Penetration Testers with a powerful and flexible platform for simulating attacks and testing the security of their systems and networks. The framework’s extensive library of pre-built exploits and payloads, modular architecture, and regular updates make it a valuable tool for ensuring an organization’s infrastructure security and protecting against real-world attacks.
What is a Metasploit?
Metasploit is a powerful and widely-used open-source framework for penetration testing, exploitation, and vulnerability scanning. It provides a suite of tools and modules for ethical hacking and testing, including exploits, payloads, auxiliary modules, and post-exploitation modules, which can be used to identify and exploit vulnerabilities in target systems or networks. It provides a controlled and structured approach to penetration testing, which can help organizations to identify and remediate potential security risks before they can be exploited by attackers. It enables security professionals to develop effective security strategies and measures to prevent real-world attacks.
Metasploit is widely used in the field of cybersecurity for both offensive and defensive purposes. It can be used for identifying vulnerabilities in systems, testing the effectiveness of security measures, and conducting simulated attacks to find weaknesses in a system. It is used on various operating systems, including Windows, Linux, and macOS.
Penetration testing using Metasploit Framework
The Metasploit Framework is an excellent tool for penetration testing as it provides a comprehensive set of features and modules that enable security professionals and Penetration Testers to simulate real-world attacks against a target system or network. It is highly customizable, allowing Penetration Testers to tailor their testing activities to meet their organization’s or customers’ specific needs. Here are a few penetration testing use cases for the Metasploit Framework.
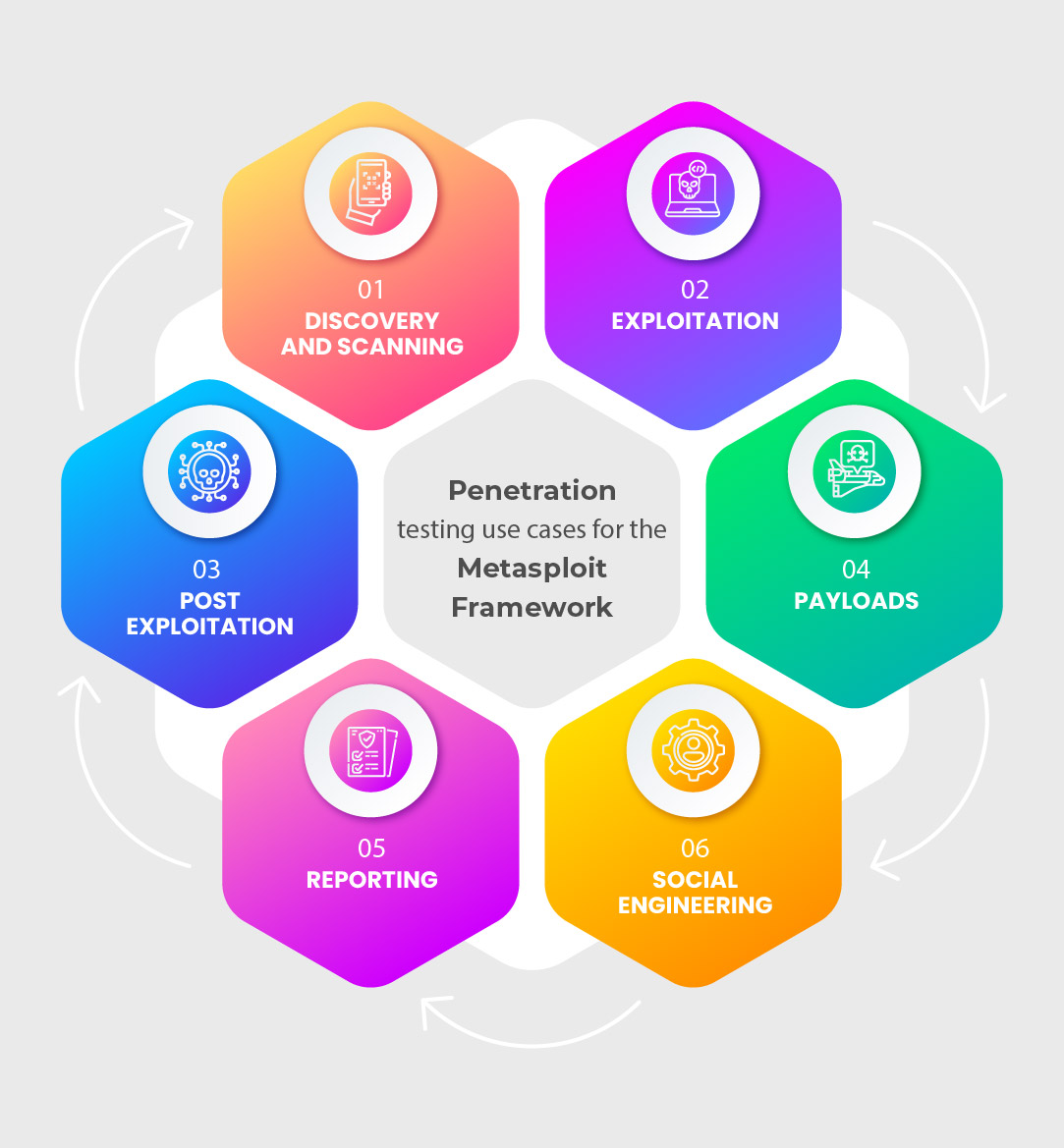
- Discovery and scanning: It can be used to scan for vulnerabilities in a target system, identify open ports and services, and gather information about the system.
- Exploitation: It provides a wide range of exploit modules that can be used to simulate real-world attacks against a target system and identify vulnerabilities that can be exploited.
- Post-exploitation: Once a system has been compromised, it can be used to perform various post-exploitation activities such as privilege escalation, lateral movement, and data exfiltration.
- Payloads: It provides a variety of payloads, such as meterpreter, that can be used to establish a remote connection to a target system, execute commands, and transfer files.
- Reporting: It can generate detailed reports of the penetration testing results, which can be used to identify areas of weakness and plan remediation strategies.
- Social engineering: It can be used to simulate social engineering attacks, such as spear-phishing attacks, to test the susceptibility of users to such attacks.
How can InfosecTrain help?
Enroll in InfosecTrain‘s RedTeam Expert online training course to learn more about the Metasploit Framework. We will provide you with structured and comprehensive guidance and practical hands-on experience on how to effectively and ethically use the framework for penetration testing. You will receive proper guidance, resources, and feedback to maximize your understanding and ability to use the tool effectively from our experienced instructors.




 1800-843-7890 (IN)
1800-843-7890 (IN) sales@infosectrain.com
sales@infosectrain.com
 1800-843-7890 (India)
1800-843-7890 (India) 
